October 2025: Domain Activity Highlights
WhoisXML API analyzed 9.6+ million domains registered between 1 and 31 October 2025 to identify the most popular registrars, top-level domain (TLD) extensions, and other global domain registration trends.
We also determined the top TLD extensions used by 38.7+ billion domains from our DNS database’s A record full file dated 4 October 2025.
Next, we studied the top TLDs of 1.1+ million domains detected as indicators of compromise (IoCs) this month.
Finally, we summed up our findings and provided links to the threat reports produced using DNS and domain intelligence sources during the period.
You can download an extended sample of the data obtained from this analysis from our website.
Zooming in on the October 2025 NRDs
TLD Distribution
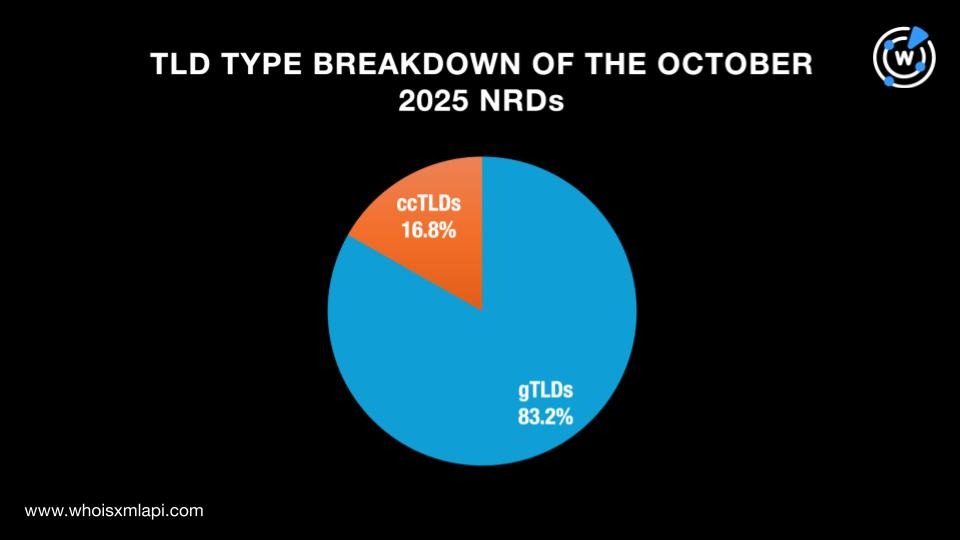
Out of the 9.6+ million domains registered in October 2025, 83.2%, up from 82.9% last month, used generic TLD (gTLD) extensions, while the remaining 16.8%, down from 17.1%, used country-code TLD (ccTLD) extensions.
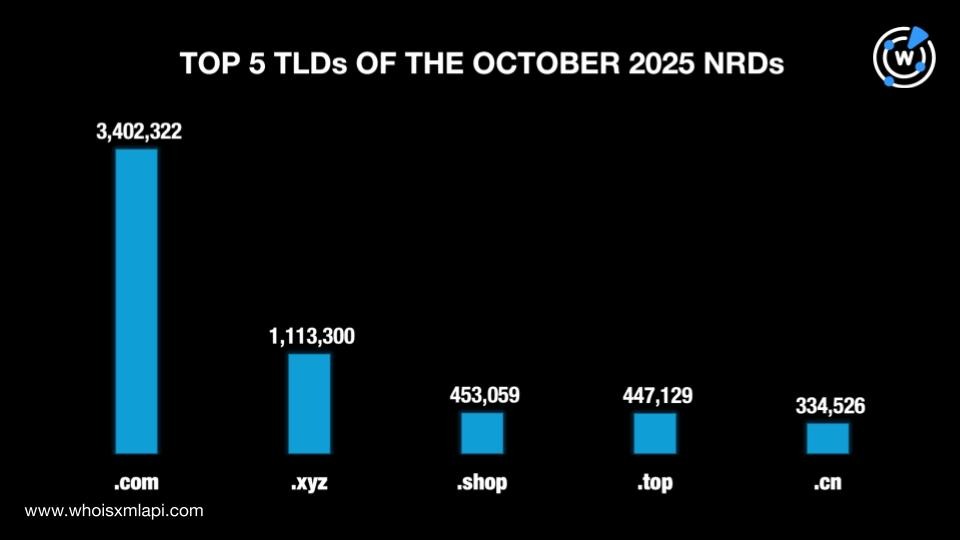
The .com TLD remained the most popular extension used by 35.4% of the total number of newly registered domains (NRDs), a little less than 35.7% in September. The other most used TLDs on the top 5 followed with a significant gap as in the previous month. Three of the remaining four topnotchers were gTLDs, namely, .xyz with an 11.6% share, .shop with 4.7%, and .top with 4.6%. The last TLD was the .cn ccTLD with a 3.5% share.
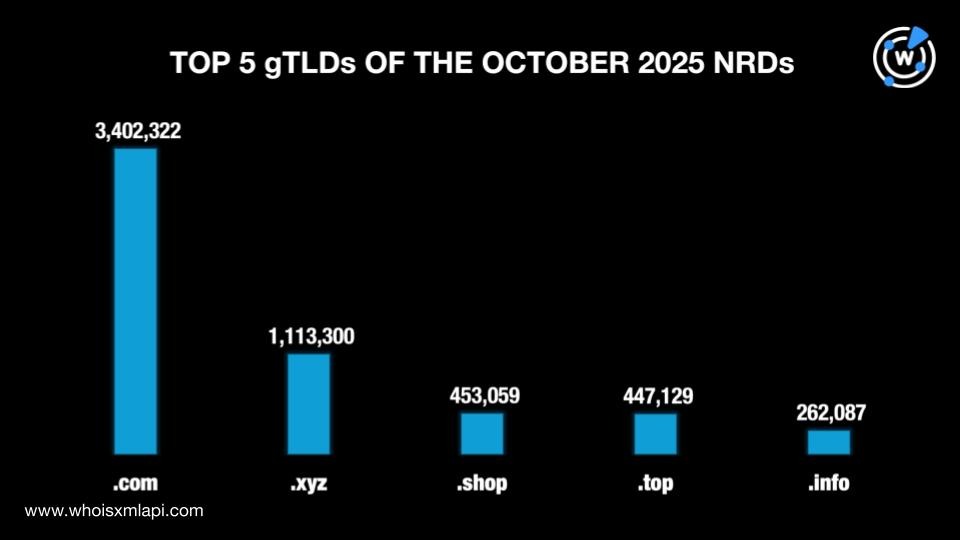
We then analyzed the October TLDs further to identify the most popular gTLDs and ccTLDs among the new domain registrations.
Out of 625 gTLDs, .com remained the most used, accounting for a 42.5% share, down from 43.1% in September. The rest of the top 5 lagged far behind. In fact, the four other gTLDs only clocked in a 28.4% share in total. The four remaining gTLDs were .xyz with a 13.9% share, .shop with 5.7%, .top with 5.6%, and .info with 3.3%.
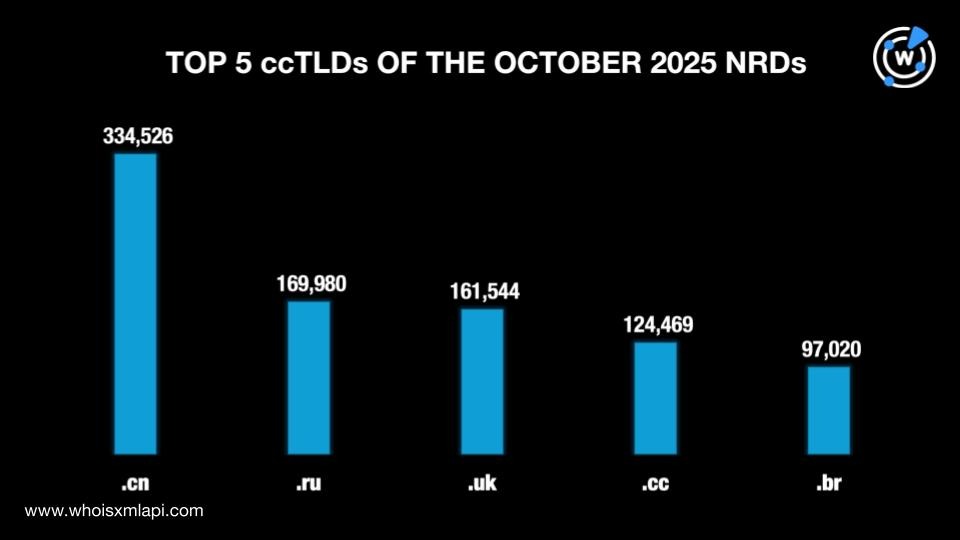
Meanwhile, .cn continued to top the list of 208 ccTLD extensions with a 20.7% share, up from 16.6% in September. The .ru ccTLD followed with a 10.5% share, up from 9.3% last month. Then came .uk with a 10.0% share, .cc with 7.7%, and .br with 6.0%.
Registrar Distribution
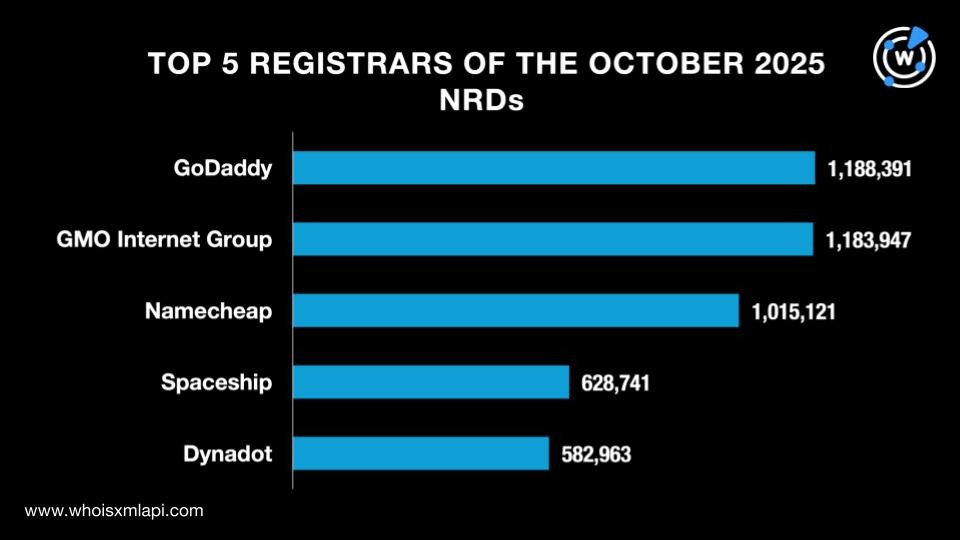
GoDaddy continued to reign supreme among the 2,578 registrars with a 12.3% share, down from 13.0% in September. GMO Internet Group ousted Namecheap from the second spot with a 12.3% share. The rest of the topnotchers were Namecheap with a 10.5% share, Spaceship with 6.5%, and Dynadot with 6.1%.
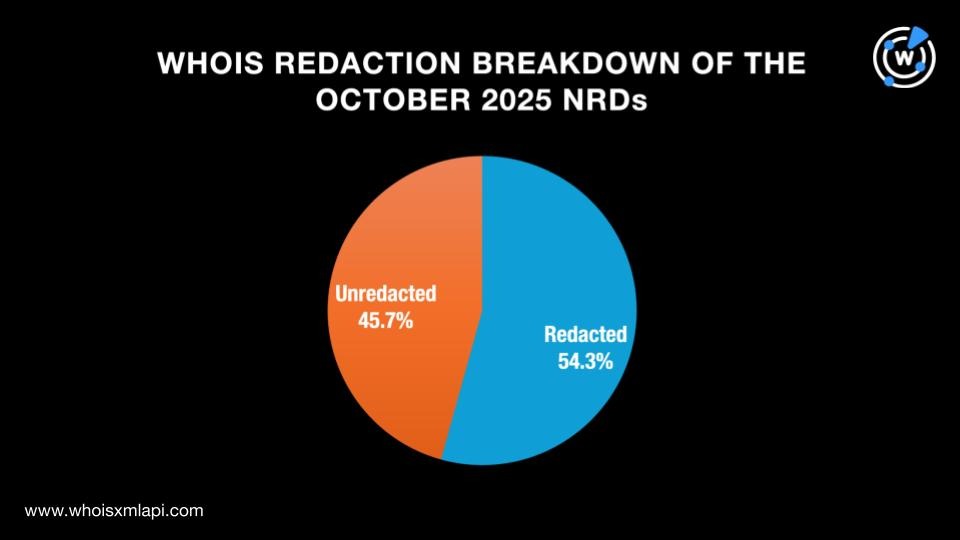
WHOIS Data Redaction
Unlike in September, fewer NRDs had unredacted WHOIS records in October, 45.7% to be exact. A total of 54.3%, meanwhile, had redacted WHOIS details.
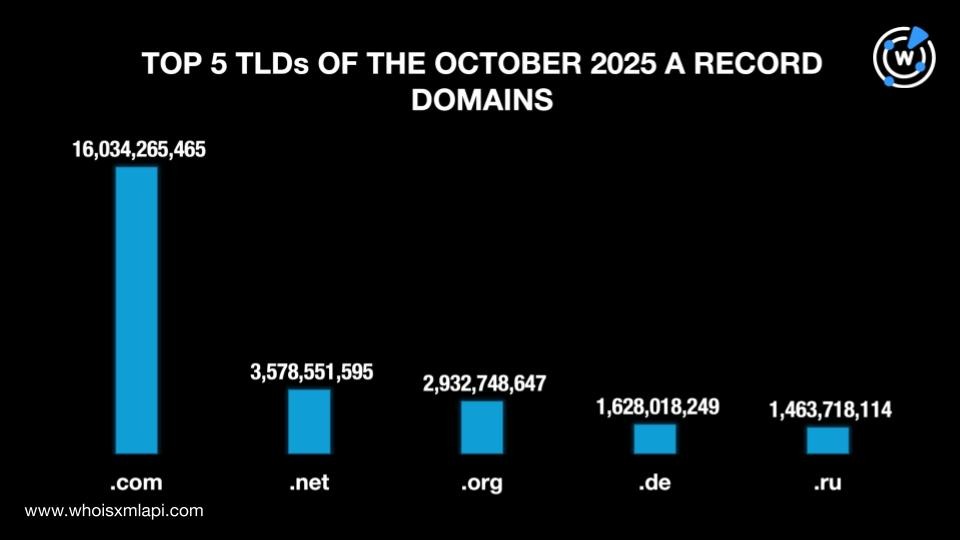
A Closer Look at the October 2025 DNS Records
Top TLDs of the A Record Domains
Next, we analyzed 38.7+ billion domains from our DNS database’s A record full file dated 4 October 2025, which included DNS resolutions from the past 365 days. We found out that 41.3% used the .com gTLD, down from 42.0% in September. The rest of the top 5 comprised two other gTLDs (i.e., .net with a 9.2% share and .org with 7.6%) and two ccTLDs (i.e., .de with a 4.2% share and .ru with 3.8%).
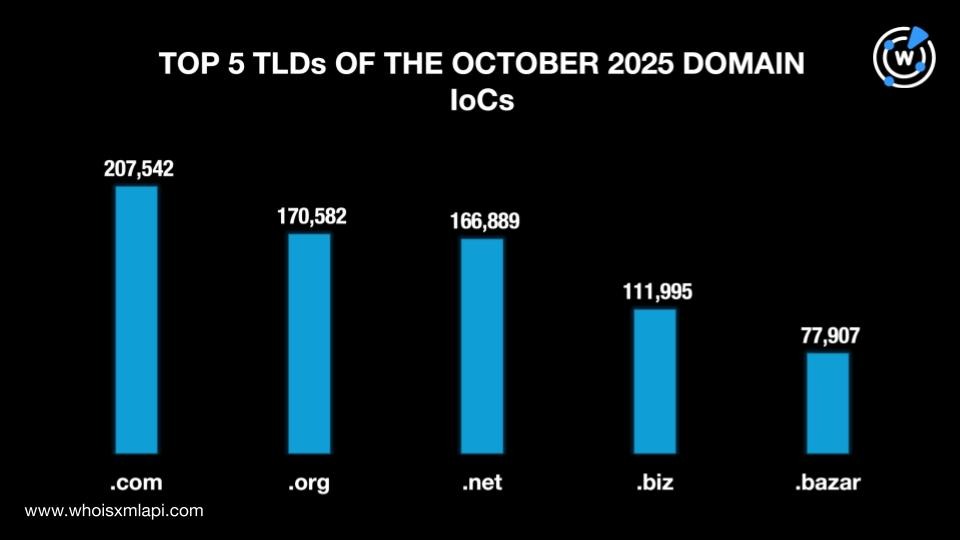
Cybersecurity through the DNS Lens
Top TLDs of the October 2025 Domain IoCs
We analyzed 1.1+ million domains tagged as IoCs for various threats detected in October. Our analysis revealed that .com remained the most popular TLD with an 18.2% share, up from 16.7% in September. The remaining top TLDs were all gTLDs as well, namely, .org with a 14.9% share, .net with 14.6%, .biz with 9.8%, and .bazar with 6.8%.
Threat Reports
Below are the threat reports we published in October 2025.
- Thumbing through the DNS Trail of the TAOTH Campaign: The TAOTH Campaign primarily targeted users across Eastern Asia using fake software update, cloud storage, and login pages to distribute malware and collect sensitive information. We analyzed eight IoCs and uncovered new artifacts along with other pertinent insights.
- Scouring the DNS for Traces of the Hiddengh0st and Winos SEO Poisoning Campaign: The Hiddengh0st and Winos search engine optimization (SEO) poisoning campaign targeted Chinese-speaking users. The attackers manipulated search rankings with SEO plug-ins and registered look-alike domains that closely mimicked legitimate software sites. We analyzed 13 IoCs and unearthed new artifacts.
- Spelunking into SVG Phishing: Amatera Stealer and PureMiner DNS Deep Dive: A rather novel phishing campaign used SVG instead of the usual PNG or JPEG/JPG files that were actually Amatera Stealer and PureMiner in disguise. They took remote control of victims’ devices to collect sensitive information, hijack computing resources, and deliver additional malware. We analyzed 26 IoCs and reported our insights.
You can find more reports created in the past months here.
Feel free to contact us for more information about the products and capabilities used to analyze domain registration events or support other use cases.





































