Yahoo! Data Breach Settlement: A Deep Dive into Fake Websites through Domain Name Monitoring

The massive Yahoo! data breach that lasted from 2012 to 2016 is one of the most notable data breaches to date, with 3 billion accounts compromised. Users’ names, birthdays, email addresses, phone numbers, and even encrypted and unencrypted security questions and answers were just some of the information stolen and potentially peddled in underground markets.
The good news is that those who have been affected can now claim benefits for the damages and losses they incurred. They can get two years of free credit monitoring or US$100–25,000 in cash as settlement for theft and potential fraud. Those interested can check if they are eligible for settlement payment by contacting the administrator of the official data breach settlement site, yahoodatabreachsettlement.com.
It seems those who suffered from the Yahoo! compromise could rest easy, right? Probably not as new threats arose shortly after the breach settlement announcement. Much like the case when Equifax announced its breach settlement details and informed victims where they could file claims, several fake websites mimicking Yahoo!’s settlement website surfaced. Those who are not careful could end up exposing even more personally identifiable information (PII) instead of obtaining remuneration from what they already lost.
To better illustrate this point, we have used various of our domain intelligence tools to study what the emerging threat environment around Yahoo! settlement site looks like and present recommendations on how to mitigate the resulting risks.
Product #1: Domain Research Suite
To start with, we performed a quick search of newly registered domains that resembled the official Yahoo! site by using “yahoodatabreachsettlement” as keyword and found several potentially harmful pages that sported .com, .net, .info, .us, and other top-level domain (TLD) extensions.
We decided to focus on the ones that sported the .com TLD, however, since the official Yahoo! website uses it — making it more likely for the 42 fake data breach settlement pages we identified to be visited by potential claimants.
By using Domain Research Suite, we compiled pertinent information about each domain (warning: we recommend not visiting or sharing any of them) in the following table:
| Domain | Date Created |
Registrant/ Registrar | Country | Email Address | IP Address |
| ahoodatabreachsettlement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| uahoodatabreachsettlement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yagoodatabreachsettlement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahhoodatabreachsettlement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahooatabreachsettlement(.com) | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodaabreachsettlement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodarabreachsettlement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatabrachsettlement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatabreachettlement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatabreachsettkement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatabreachsettleent(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatabreachsettlememt(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatabreachsettlemen(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatabreachsettlemet(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatabreachsettlemnt(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatabreachsettlemrnt(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatabreachsettlemwnt(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatabreachsettlenent(.)com | September 1, 2019 | Incomplete data |
|
| 199.59.242.152 |
| yahoodatabreachsettlrment(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatabreachsetttlement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatabreachsttlement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatabreacsettlement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatabreahsettlement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatabreavhsettlement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatabreaxhsettlement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatabreschsettlement(.)com | September 26, 2019 | Incomplete data |
|
| 199.59.242.152 |
| yahoodatabteachsettlement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatareachsettlement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodatebreachsettlement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| yahoodtabreachsettlement(.)com | August 31, 2019 | Super Privacy Service LTD c/o Dynadot | UNITED STATES | [email protected] | 199.59.242.152 |
| theyahoodatabreachsettlement(.)com | September 1, 2019 | XINNET TECHNOLOGY CORPORATION |
| [email protected] | 199.59.242.152 |
| yahoodatabreachsettle(.)com | September 1, 2019 | XINNET TECHNOLOGY CORPORATION |
| [email protected] | 199.59.242.152 |
| yahoodatabreachsettlements(.)com | September 1, 2019 | XINNET TECHNOLOGY CORPORATION |
| [email protected] | 199.59.242.152 |
| yahoodatabreech(.)com | September 1, 2019 | XINNET TECHNOLOGY CORPORATION |
| [email protected] | 199.59.242.152 |
| yahoodatabeeachsettlement(.)com | September 5, 2019 | Chengdu West Dimension Digital Technology Co., Ltd. | CHINA |
| 103.224.182.242 |
| yahoodataberachsettlement(.)com | September 5, 2019 | Chengdu West Dimension Digital Technology Co., Ltd. | CHINA |
| 103.224.182.242 |
| yahoodatabraechsettlement(.)com | September 5, 2019 | Chengdu West Dimension Digital Technology Co., Ltd. | CHINA |
| 103.224.182.242 |
| yhaoodatabreachsettlement(.)com | September 5, 2019 | Chengdu West Dimension Digital Technology Co., Ltd. | CHINA |
| 103.224.182.242 |
| yshoodatabreachsettlement(.)com | September 5, 2019 | Chengdu West Dimension Digital Technology Co., Ltd. | CHINA |
| 103.224.182.242 |
| yahoobreachdatasettlement(.)com | September 9, 2019 | Domains By Proxy, LLC | UNITED STATES | [email protected] | 45.33.2.79 96.126.123.244 45.33.23.183 198.58.118.167 45.79.19.196 45.56.79.23 |
| yahoodatabreachaettlement(.)com | September 11, 2019 | Domains By Proxy, LLC | UNITED STATES | [email protected] | 200.63.47.3 |
| yahoodatabreaachsettlement(.)com | September 23, 2019 | Privacy Protect, LLC (PrivacyProtect.org) | UNITED STATES | [email protected] | 45.33.2.79 198.58.118.167 96.126.123.244 45.79.19.196 45.56.79.23 45.33.23.183 |
Notice that all of the domains are only slightly misspelled variations of the real domain — a telltale sign that they are malicious or, at the very least, illegitimate links. It is not uncommon, after all, to obtain phishing victims via mistyped URLs. In this case, phishers may have registered domains that closely resembled the Yahoo! data breach settlement site to entrap users who may wish to file for claims. That way, the phishers could instead obtain the claimant’s Yahoo! credentials and pocket the fees.
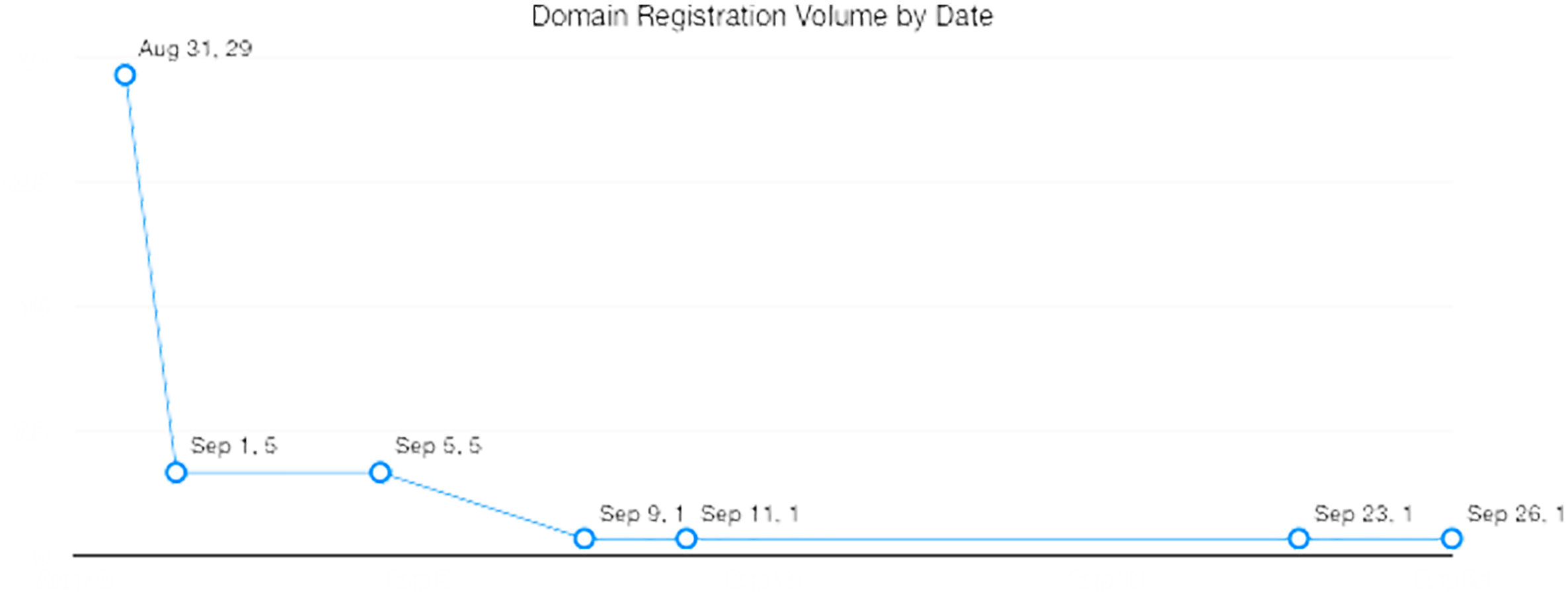
The following is a summary of our observations:
- Around 79% of the domains were registered between 31 August and 1 September 2019 — 3-4 days
before the official announcement was made on 4 September. The remaining 21% were registered
after the announcement between 5-26 September 2019. The following chart shows the number of
domain registrations by date of creation:
![The following chart shows the number of domain registrations by date of creation The following chart shows the number of domain registrations by date of creation]()
- 29 of the domains were registered on 31 August 2019
- 5 each were created on 1 and 5 September 2019
- 1 each were registered on 11, 23, and 26 September 2019
- Based on recorded registrant or registrar for domains that were registered anonymously or
privately:
- 27 were under Super Privacy Service LTD c/o Dynadot
- 5 were under Chengdu West Dimension Digital Technology Co., Ltd.
- 4 were under Xinnet Technology Corporation
- 2 were under Domains By Proxy, LLC
- 2 had incomplete data
- 1 was under Privacy Protect, LLC (PrivacyProtect.org)
- Based on country of registration:
- 31 were hosted in the U.S.
- 6 were located in China
- 6 did not indicate their location
- While a majority of the domains had corresponding email addresses (i.e., matched their domain
names), some used the addresses of their registrars, namely:
- [email protected] for those owned by Xinnet Technology Corporation
- [email protected] for that owned by Privacy Protect, LLC (PrivacyProtect.org)
- Based on the IP address:
- 33 shared the IP address 199.59.242.152 (all domains registered by Super Privacy Service LTD c/o Dynadot and Xinnet Technology Corporation, along with the 2 domains with incomplete data)
- 5 shared the IP address 103.224.182.242 (all domains registered by Chengdu West Dimension Digital Technology Co., Ltd.)
- 2 shared multiple IP addresses including 45.33.2.79, 96.126.123.244, 45.33.23.183, 198.58.118.167, 45.79.19.196, and 45.56.79.23 (all domains registered by Domains By Proxy, LLC)
- 1 used the IP address 200.63.47.3 (registered by Privacy Protect, LLC [PrivacyProtect.org])
What the Results Reveal
This ratio of domain registration volume (peaking before the official announcement and dwindling afterward) is not surprising. Phishers would, after all, want to have their fake pages up and ready when potential claimants come looking for more details on how to file for damages and be the first in line.
The disparity between the number of domains (42) and registrants (6), along with being registered at around the same dates is indicative of bulk registration.
Despite leaving out information in their WHOIS records, yahoodatabreschsettlement(.)com and yahoodatabreschsettlement(.)com were most likely registered by using Super Privacy Service LTD c/o Dynadot as well since their creation could be traced to the same IP address —199.59.242.152— as all the other domains owned by the registrant.
It’s also worth noting that Super Privacy Service LTD c/o Dynadot and Xinnet Technology Corporation shared the same IP address. That said, even if the domains registered by Xinnet Technology Corporation did not indicate where these were hosted, it would be safe to assume they are in the same country — the U.S.
Additional Research and Investigation
We crossed-checked our initial domain registration findings with other WHOIS research results and found these additional bogus websites:
- wwwyahoodatabreachsettlement(.)com
- yahoodatabreach(.)com
- yahoodatabreachlawsuit(.)com
- yahoodatabreachsetlement(.)com
- yahoodatabreachsettelment(.)com
- yahoodatabreachsettement(.)com
- yahoodatabreachsettlement(.)com
- yahoodatabreachsettlment(.)com
- yahoodatabreachssettlement(.)com
Random checks on each site’s registration date revealed that these were registered even earlier than 31 August 2019. It is possible that some no longer exist.
One particular site — yahoodatabreach(.)com — proved interesting as it was initially created on 8 March 2017, two years before a decision was made regarding the terms of the Yahoo! breach settlement. This site’s registration was renewed on 3 February 2019, although it was deleted soon afterward.
Some of the domains were also registered a few years ago. Cybercriminals may have been anticipating that affected users would look for details about the compromise and were hoping that they would land on their fake websites.
Product #2: Reverse IP API
Having identified the recurring IP addresses that figured in the reverse WHOIS searches we conducted, we took a closer look at the most prominent — 199.59.242.152 via Reverse IP API. This IP address has an estimated age of 3,235 days (more than 8 years old). We tracked down the organization that owns it, and it turned out to be a domain parking platform company.
While domain parking isn’t illegal, cybercriminals often buy parked domains to host their malicious sites. That could very well have been the case here. Those behind the fake Yahoo! data breach settlement sites could have purchased the .com domains we uncovered in bulk to save on costs, which explains the same registration date.
In most cybersecurity cases, attack prevention is achieved by blocking specific IP addresses on the network side. This approach prevents users from inadvertently visiting potentially harmful sites or malicious individuals from gaining access to systems and data stored within the said network. It may thus be a good idea for organizations to block the IP addresses tied to the fake sites mentioned in this post.
Product #3: Domain Reputation API
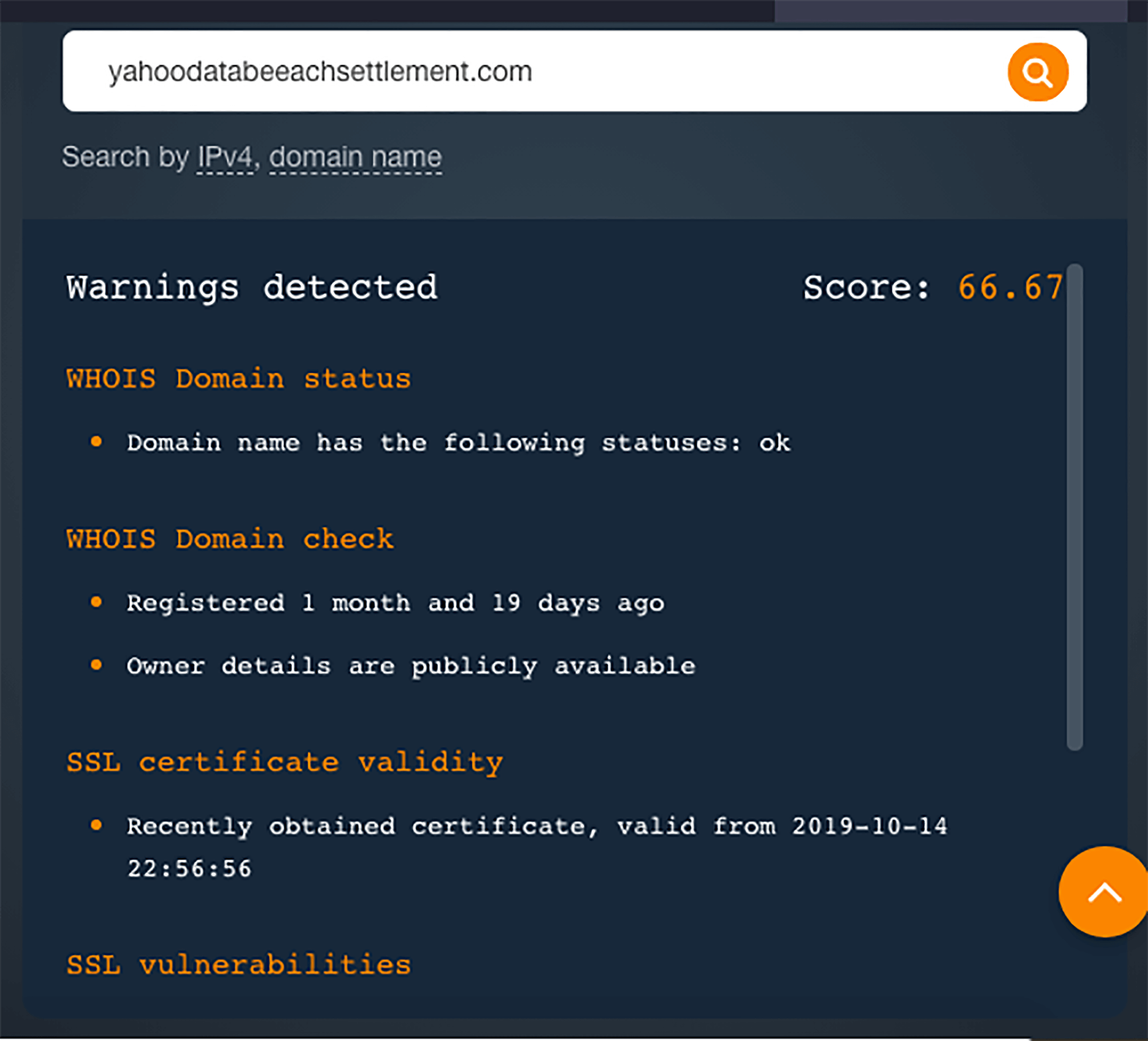
To better showcase the malicious nature of these online properties mimicking Yahoo!’s settlement site, we used Domain Reputation API to analyze two of the spoofed domains and give them a score between 0 and 100. Note that the ideal is 0, which indicates that the site is safe to access.
- Yahoodatabeeachsettlement(.)com had a reputation score of 66.67. A warning of its newness was
given off by the API along with its very recent SSL certificate issuance and
vulnerabilities.
![Product #3: Domain Reputation API Product #3: Domain Reputation API]()
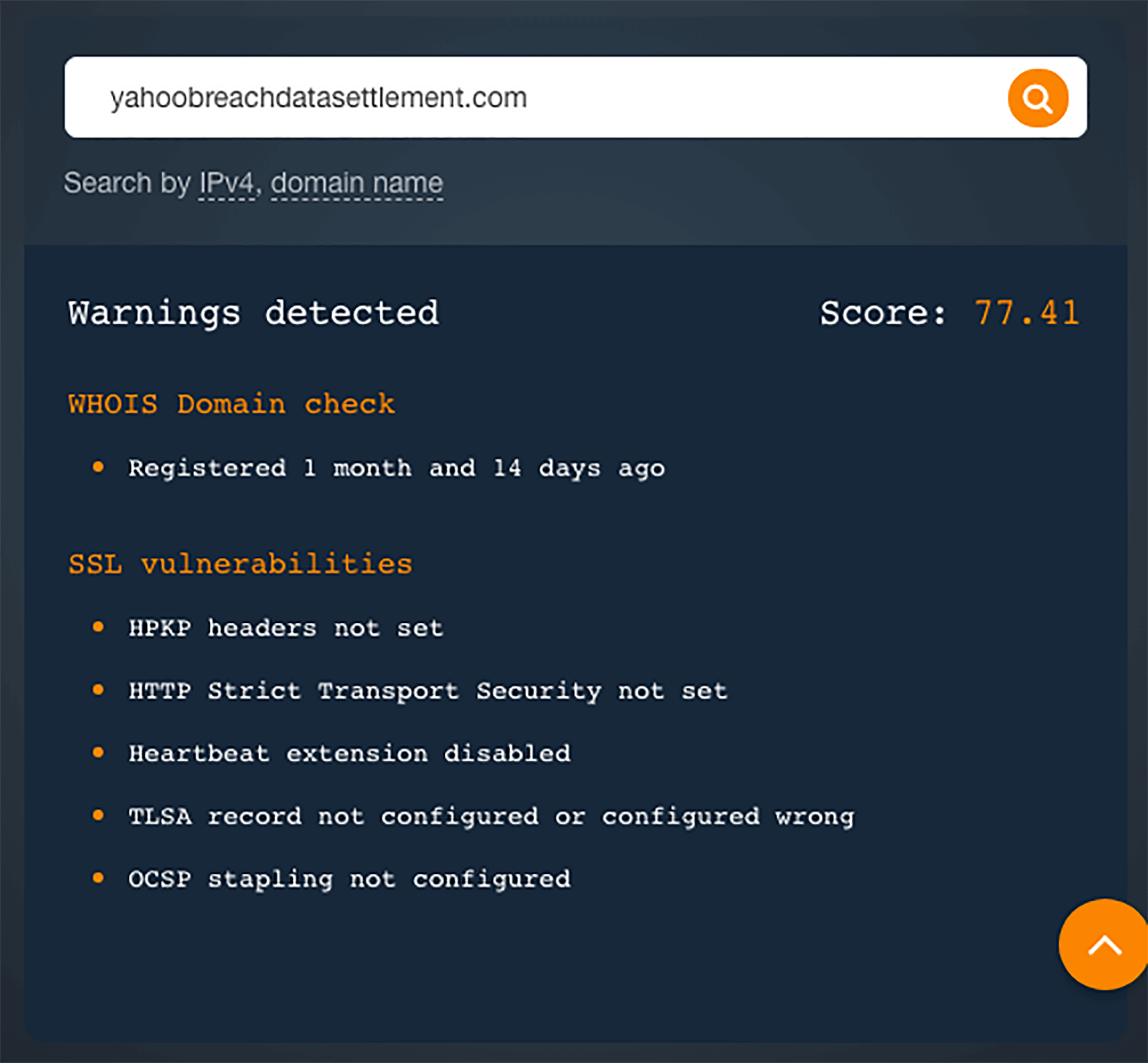
- Yahoobreachdatasettlement(.)com had a reputation score of 77.41. Warnings about its young age
and SSL vulnerabilities were also cited.
![Product #3: Domain Reputation API Product #3: Domain Reputation API]()
Conclusion and Best Practices
Based on our IP and WHOIS search deep dives, most of the potentially malicious domains seem to be parked only. However, some cyber attacks could still be in the making.
Regardless of the motivation, one thing remains clear: Bulk domain registration is one means by which typosquatters or cybersquatters make money.
The owners of the spoofed domains could be waiting for other bad guys to buy them to be used in phishing attacks. It is, after all, easy to put up a site that would collect claimants’ Yahoo! Credentials.
Claimants can watch out for phishing attacks by following these best practices:
- Verify if the link they’re trying to access is indeed the official Yahoo! data breach settlement website. They can refer to the official Yahoo! site for more details.
- Should they receive an email from someone claiming to be from Yahoo!, they can call the company’s office to verify the communication first. If the sender’s email address appears in the table above, it’s probably a phishing email that needs to be deleted immediately.
- Check for typos and grammatical errors in the sender’s email address, message content, and subject line. These are usually found in phishing emails.
- Avoid clicking on links embedded in emails and downloading attachments from unknown senders. This action can unknowingly land users on malicious sites.
- Use a security solution that blocks spam and malware, along with access to known malicious websites.
On the other hand, Yahoo! and organizations that want to better protect claimants and others against phishing, typosquatting, and website spoofing can rely on the variety of tools offered by Domain Research Suite:
- Brand Monitor allows users to detect potential trademark infringers and other brand abusers. Using its typos feature, users can automatically generate a list of misspelled variations of their domain for further investigation.
- With Registrant Monitor, users can keep tabs on registrants who have committed wrongdoings in the past.
- Domain Monitor, meanwhile, can help users keep track of domains with checkered pasts, so any time these are reused in attacks, they could be quickly taken down.
- Reverse WHOIS Search lets users gather detailed WHOIS information corresponding to a particular “Search term” on a domain as contained in WHOIS records — names, phone numbers, email addresses, etc.
- WHOIS History Search makes it possible to dig deeper into the history of a domain to check for all its past owners as well as other modifications over the years.
We hope you found this cybersquatting investigation of Yahoo!’s settlement site useful. For more information about Domain Research Suite, feel free to contact us or sign up and give the suite a try.