Can Domain Intelligence Help Healthcare Service Providers Combat Data Breaches?

Hospitals and other healthcare service providers have been among criminals’ favorite breach targets in the past few years. One of what has been dubbed the biggest data breaches of the 21st century involved a healthcare insurance giant — Anthem.
The Anthem breach reported in February 2015 was said to have exposed around 78.8 million customer records. This incident put the personal data of the insurer’s clients at risk of theft. The question is: could Anthem have prevented the breach? This downloadable white paper will take a look at the case in greater detail and illustrate how Domain Research Suite can help.
Table of contents
- The Attack: The Biggest Healthcare Data Breach So Far
- The Case Facts: How Anthem’s Database Was Compromised
- A Possible Solution: Could Domain Research and Monitoring Tools Have Helped in Anthem’s Case?
- The Verdict: Lessons Learned from the Anthem Breach
The Attack: The Biggest Healthcare Data Breach So Far
Hospitals and other healthcare service providers are prime cyber attack targets because they collect and store vast amounts of patients’ and employees’ personal data. This information usually ends up being used to steal from their owners or sold to the highest bidders in underground markets.
Stolen healthcare records often contain financial information that cyber attackers can use to purchase goods and services without spending a dime from their own wallets. Those that are sold to other criminal entities can be used to obtain prescription drugs and medical equipment. Those are just a few examples of where stolen healthcare data ends up in; there are tons more.
In some countries, the healthcare industry is considered a critical infrastructure operator, making it an ideal target for those who wish to cause damage on a massive scale. This scenario is more like the case for Anthem according to the federal investigation that followed in its wake.
The Victim
Anthem is the second-largest healthcare insurance provider in the U.S. that serves more than 78 million customers.
The Attack Vector
Investigations into the Anthem breach revealed that the attackers got into the target’s network when an employee from one of its subsidiaries opened a phishing email. The credentials obtained from this were then used to infiltrate the organization’s data warehouse.
The Bait
Not much detail about the actual content of the phishing email used in the attack made its way into reports. What is clear is that whoever was tricked into sharing his credentials gave the attackers a way into Anthem’s network.
The Case Facts: How Anthem’s Database Was Compromised
As has been said, the attackers compromised Anthem’s network through a phishing email opened by an employee of one of its many subsidiaries way back in February 2014.
For months, the attackers had moved laterally throughout the Anthem network before the first signs of suspicious database activity was seen in December 2014. To address the situation, the organization issued a memo to alert its security personnel about suspicious log-ins. By that time, the attackers have already acquired a database administrator’s log-in credentials — the key to obtaining the personal records of Anthem’s customers and employees.
Among the stolen records were individuals’ names, birthdays, medical ID and social security numbers, street and email addresses, and employment information, including even income data. Although no evidence of financial fraud tied to the breach was found, Anthem immediately reported the incident to the authorities and informed those affected.
All hospitals and healthcare service providers in the U.S. are ultimately mandated to abide by the Health Insurance Portability and Accountability Act (HIPAA). One of its provisions is the HIPAA Breach Notification Rule, which requires covered entities and their business associates to notify the authorities following a breach of unsecured protected health information.
Due to the vast victim pool, a team of investigators led by seven state insurance commissioners across the U.S. was to conduct a nationwide examination of the breach. For its part, Anthem hired Mandiant to conduct its own internal investigation into the cyber attack. Both parties concluded after some time that the attack was state-sponsored.
Anthem has since invested as much as US$260 million to beef up the security of its IT infrastructure. It also offered identity theft protection services to its members. In October 2018, the organization agreed to pay US$16 million to settle a privacy violations case that the U.S. government wanted to charge it with despite non-admittance of any wrongdoing. As part of the agreement, Anthem was also asked to undertake a “corrective action plan” to enhance its internal security procedures and practices, which will be monitored by the government.
Just this May, a Chinese hacker was identified as one of the perpetrators of the Anthem breach. Fujie Wang and other unnamed members of a China-based hacking group were charged with four counts of conspiracy to commit fraud, identity theft, and computer hacking. The group was found to have had links to attacks on a tech company, a basic materials firm, and a communications giant even if these weren’t included in the indictment. Wang has, however, yet to be apprehended.

A Possible Solution: Could Domain Research and Monitoring Tools Have Helped in Anthem’s Case?
Phishing is probably one of the oldest yet most reliable tricks of the cybercriminal trade. In Anthem’s case, the hackers are likely to have made use of a very believable spearphishing email aiming to get an employee with access to the target’s database to give out his credentials.
Because we don’t have much to rely on, such as a phishing email sample used in the breach, we need to make some reasonable assumptions. The email needs to have come from a source that the recipient would likely be compelled to open to be effective. This source could have been a higher-up in the company (typically mimicked sources in spearphishing attacks such as in business email compromise [BEC] schemes), a contact person from a third party (e.g., partner, supplier, authority such as the U.S. Department of Health and Human Services [HHS], etc.), an organization the company is part of (e.g., the HITRUST Alliance, etc.), a co-employee, or other trusted people.
Other elements of an effective phishing email include an enticing subject or content that could benefit the recipient in one way or another.
In this case, let’s assume a hard-to-ignore sender was the key such as the HITRUST Alliance (Anthem was a member of this). The victim could have been compelled to download a specially crafted file attachment (a sophisticated piece of malware capable of lateral movement throughout the target network) disguised as an important document from the alleged sender. All it took to infiltrate Anthem’s network was opening the said document and the rest, as they say, is history.
Under the circumstances suggested, could the attack have been prevented though? Yes, some tools can help companies verify the source of an email. One such tool is WHOIS API. With it, Anthem could have created a blacklist of email addresses, URLs, domains, and more to prevent unauthorized access to its network. It could also have created a white list that only gives access to authorized entities or persons.
Let’s see how you can create such lists using the step-by-step guide below.
- Visit https://whoisapi.whoisxmlapi.com/ and scroll down until you see the Give the API a Try section
where you can enter an IP address or a domain name.
![Visit https://whoisapi.whoisxmlapi.com/ and scroll down until you see the Give the API a Try section where you can enter an IP address or a domain name. Visit https://whoisapi.whoisxmlapi.com/ and scroll down until you see the Give the API a Try section where you can enter an IP address or a domain name.]()
- Let’s say you want to make sure that the email you just received is indeed from the HITRUST Alliance (IMPORTANT NOTE: This case presents a hypothetical scenario, so we are not saying the email used to hack Anthem’s network in any way indicated this). Type the organization’s domain — hitrustalliance.net — in the Search field.
- Hit Enter. The tool automatically provides results in XML format so you should see something like
this:
If you are more comfortable working with the JSON format, click the JSON button. That would give you something like this:
![The tool automatically provides results in XML format so you should see something like this The tool automatically provides results in XML format so you should see something like this]() If none of the raw formats work for you, click the Preview button to see the results in formatted text. You should see something similar to this:
If none of the raw formats work for you, click the Preview button to see the results in formatted text. You should see something similar to this:![If you are more comfortable working with the JSON format, click the JSON button If you are more comfortable working with the JSON format, click the JSON button]()
![If none of the raw formats work for you, click the Preview button to see the results in formatted text If none of the raw formats work for you, click the Preview button to see the results in formatted text]()
- Cross-check the domain information on the WHOIS record with that on the organization’s (sender) website.
Make sure, for instance, that the street address and other details on the record match those on its
website. For added peace of mind, as some mask their domains, you can use a tool like Email Verification
API. This tool helps users validate and verify email addresses.
![This tool helps users validate and verify email addresses. This tool helps users validate and verify email addresses.]()
- Our comparison shows that nothing is at odds. If, however, the sender’s domain doesn’t belong to HITRUST Alliance as shown on its WHOIS record, don’t even open it. Instead, include its domain in your blacklist.
- If it does, it may be a good idea to include all of the HITRUST Alliance’s legitimate domains in a white list. This same white-listing process can be done for all certified authorized users while those deemed suspicious or outright malicious should be blacklisted from accessing any of your public-facing properties (e.g., websites, portals, etc.).
- Black- and white-listing URLs is not a bulletproof solution to the many threats that can put healthcare service providers at significant risk, however. Blacklisting is an excellent method for addressing the dangers that phishing poses. Users can, for instance, obtain a list of all known phishing websites to be included in their blacklist. That way, even employees who are prone to clicking URLs embedded in emails from unknown or spoofed senders, won’t make the organization a phishing victim. Phishing is, after all, one of the leading causes of data breaches in the healthcare sector. White-listing, meanwhile, would make sure that none of the emails from trusted partners and collaborators would end up in any user’s junk or spam folder.
- In today’s dynamic and increasingly sophisticated threat landscape, proactive measures that require vigilant monitoring of network access are critical. An excellent means to do that is using tools like Domain Research Suite. This product comes with various search and monitoring tools that allow users to protect their entire domain from unwelcome intrusion. With its various features, organizations can identify malicious URLs that they can then block. They can also monitor suspicious URLs - without exerting much time and effort - for relations to malicious activities. Once ties are confirmed, it should be easy to prohibit them from gaining access to your online properties.
Digging into the Capabilities of Domain Research Suite
To gain a better sense of how Domain Research Suite’s roster of applications can help healthcare organizations enhance their cybersecurity posture, take a look at the following demonstrations:
Reverse WHOIS Search
Let’s say you received a message from a supposed HITRUST Alliance employee asking you for access to your company’s patient records. You noticed that instead of hitrustalliance.net, the domain name in the sender’s email address is hitrust.net. Should you abide by the sender’s wish? Of course not. You need to vet his claims first without offending him should his claim be valid. You can use Reverse WHOIS Search to do that. Just copy the sender’s domain name into the input field then click Search.
You should see something like this:
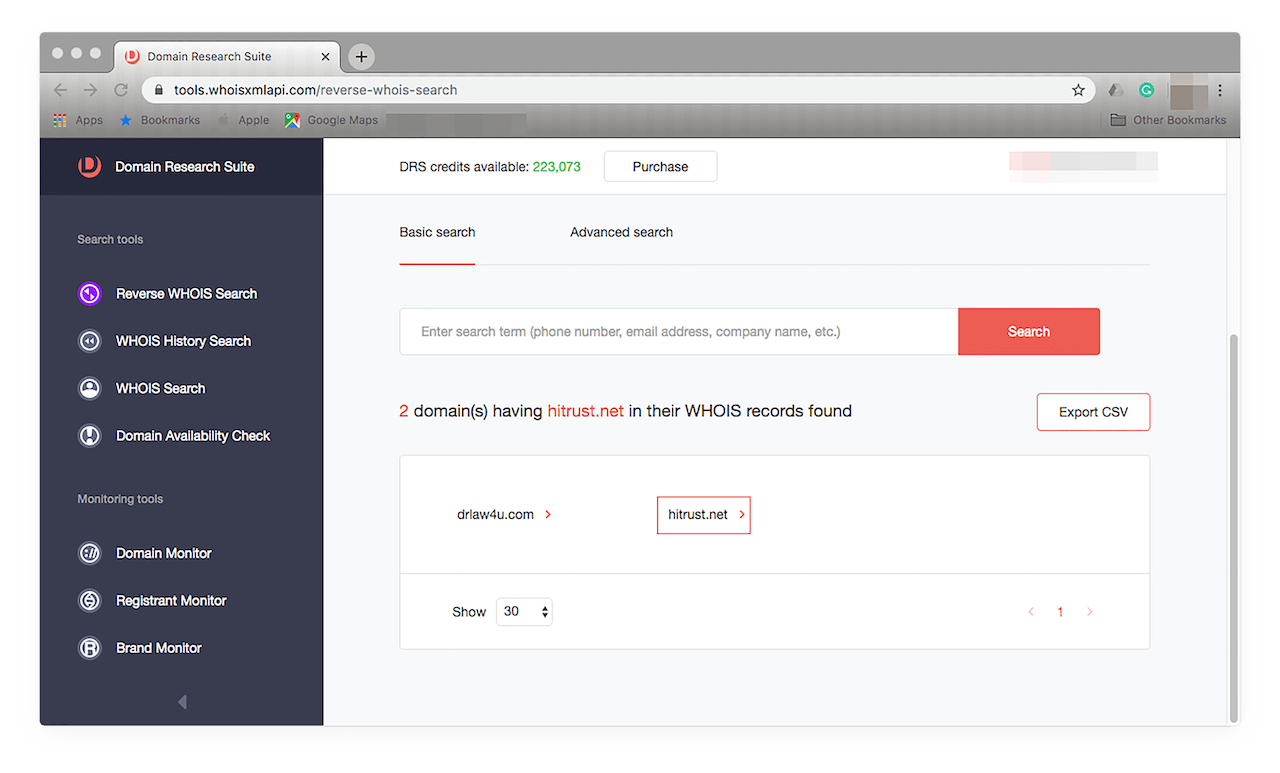
This report tells you that hitrust.net is an active domain name. That’s still not enough information, however. So let’s use the next tool.
WHOIS History Search
To access this, click its name from the menu on the left. You should see this afterward:
As with the first tool, type the domain name in the input field then click Search. You should see query results like this:
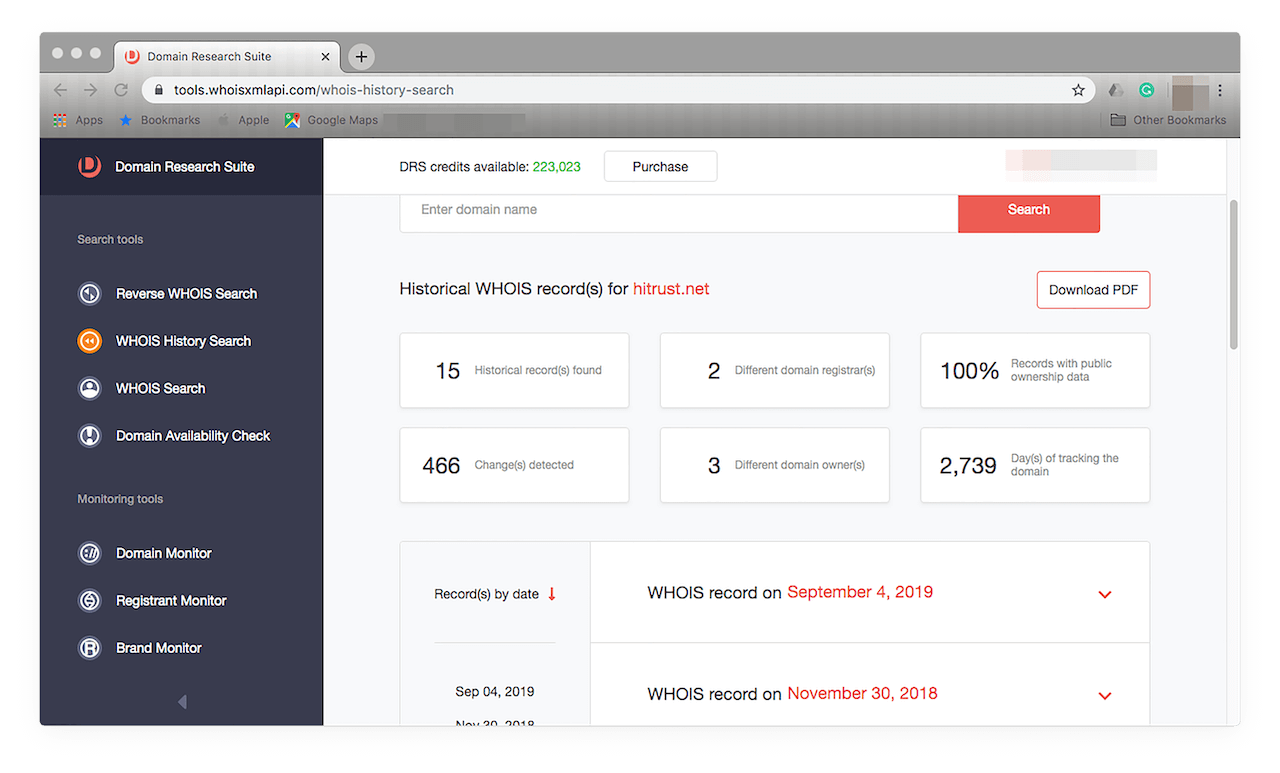
This tool allows you to see all of the modifications the domain has undergone since its first use. You see, for instance, that it is around 7.5 years old. It has undergone close to 500 changes, including two registrar and three owner modifications. The records are arranged from newest to oldest.
Take a look at the most current record to see more details on its owner by clicking the down arrow (∨) beside the latest date. You should see something like this:
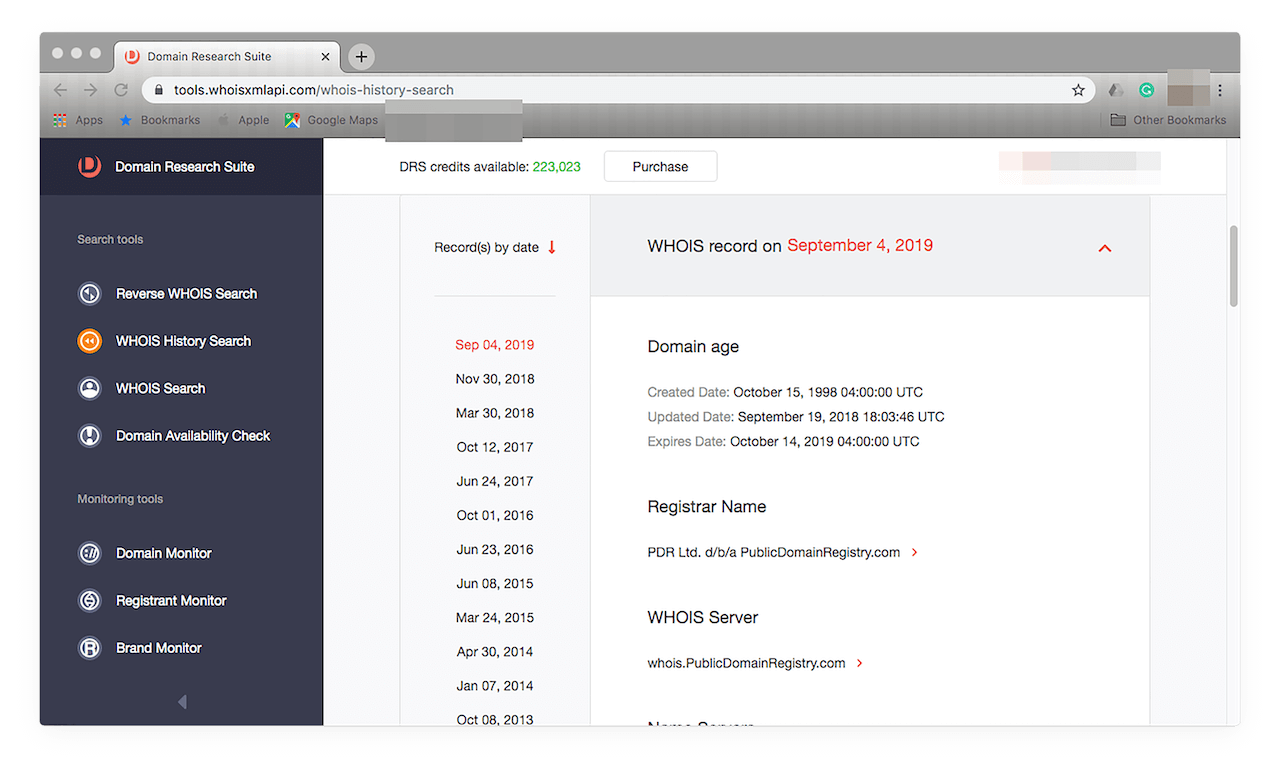
Browse through the details, specifically the registrant’s, to find out if the sender is indeed from the HITRUST Alliance.
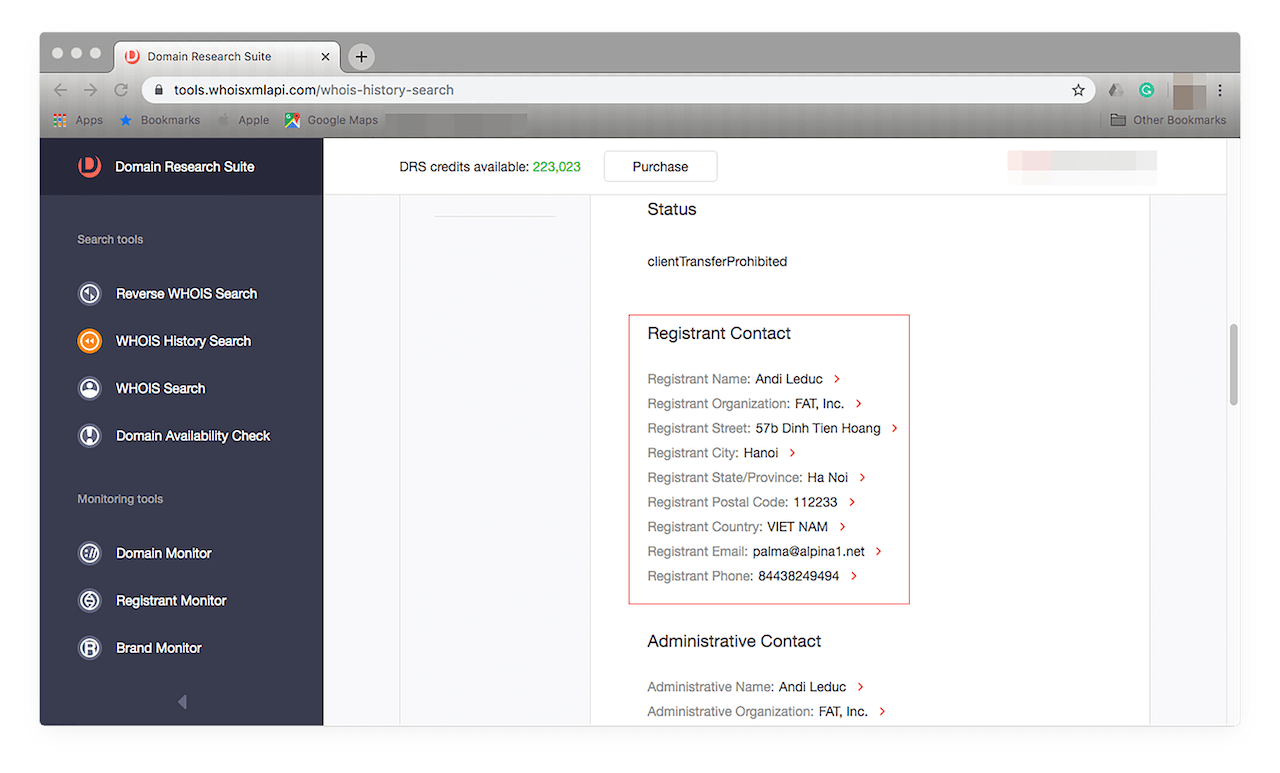
(NOTE: The domain hitrust.net is NOT MALICIOUS, we just used it for demonstration purposes.)
You find out that the HITRUST Alliance doesn’t own the domain. The domain could have been compromised by an attacker and used to send you a malicious email. Mark the message as spam or junk or include the domain in your blacklist so no one in your company can get scammed in the future.
Brand Monitor
This tool uses a brand name as a search term. You can monitor potential copycats of your domain with its ‘typos’ feature. That way, your organization can stay protected from website spoofers, phishers, and typosquatters. All you need to do is access the tool from the menu on the left-hand side of your screen. That should open this window:
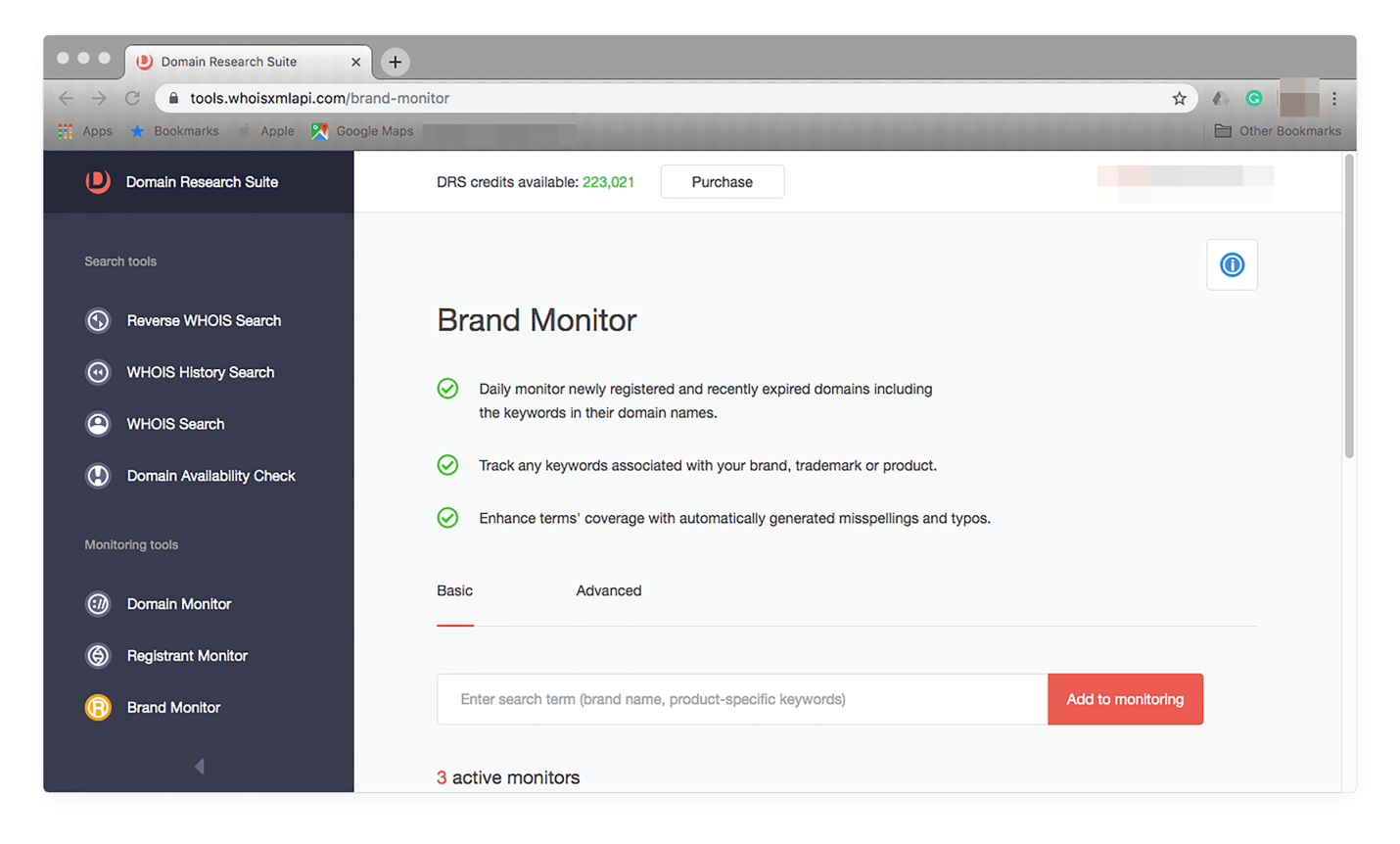
Add your brand by typing it in the input field and clicking Add to monitoring. You should see the brand in your tracker:
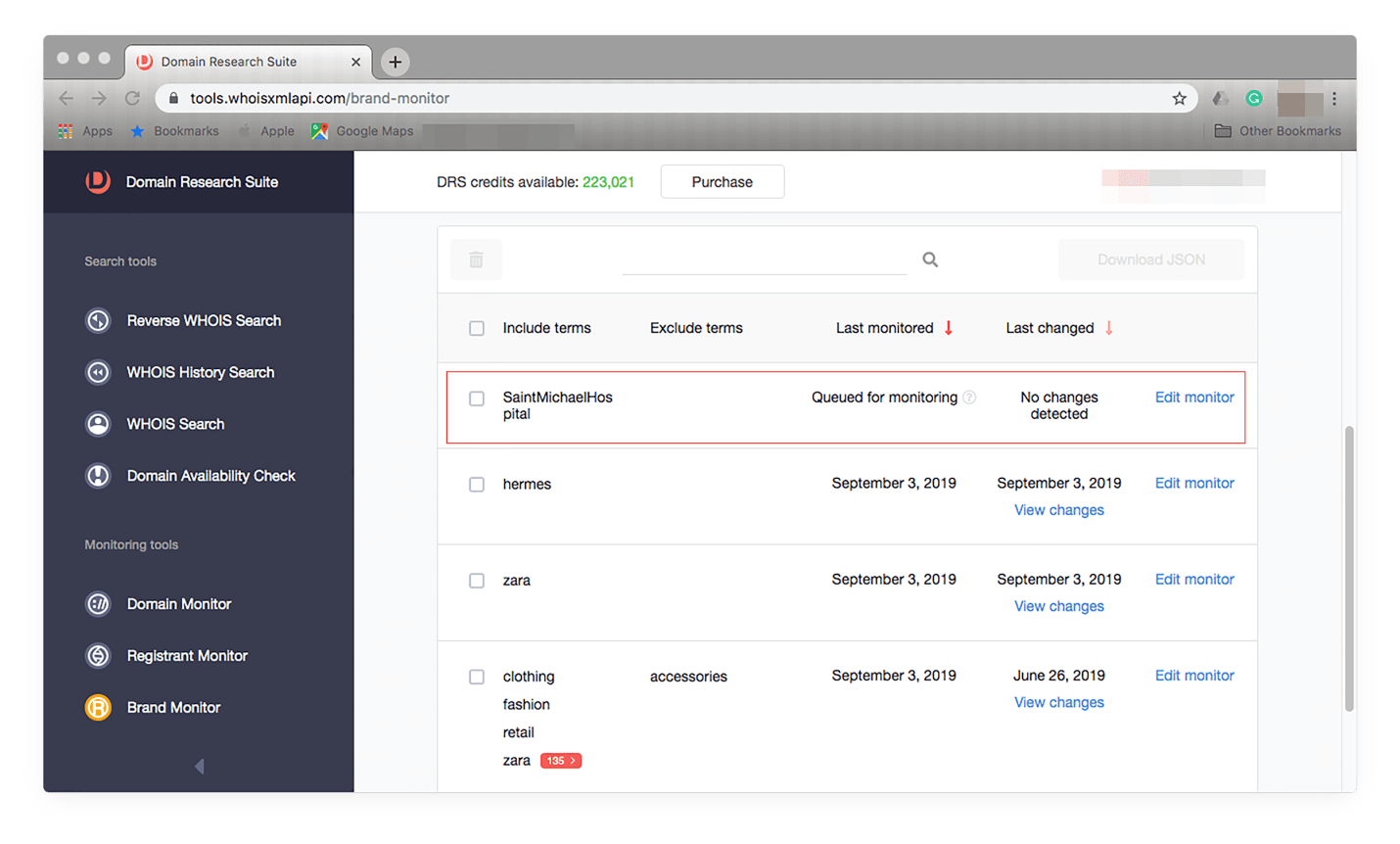
To see Brand Monitor in action, you can refer to this investigative post that discusses its brand protection features.
Domain Monitor
This tool lets users keep tabs on domains of interest, be it for cybersecurity, branding, marketing, or other purposes. Say, you’re still unsure of the intentions of the individual who used hitrust.net domain, you can include it in your monitoring list. First, click Domain Monitor on the menu on the left. You should see this window:
Type the domain name in the input field then click Add to monitoring. You should see this on your list of domains to track:
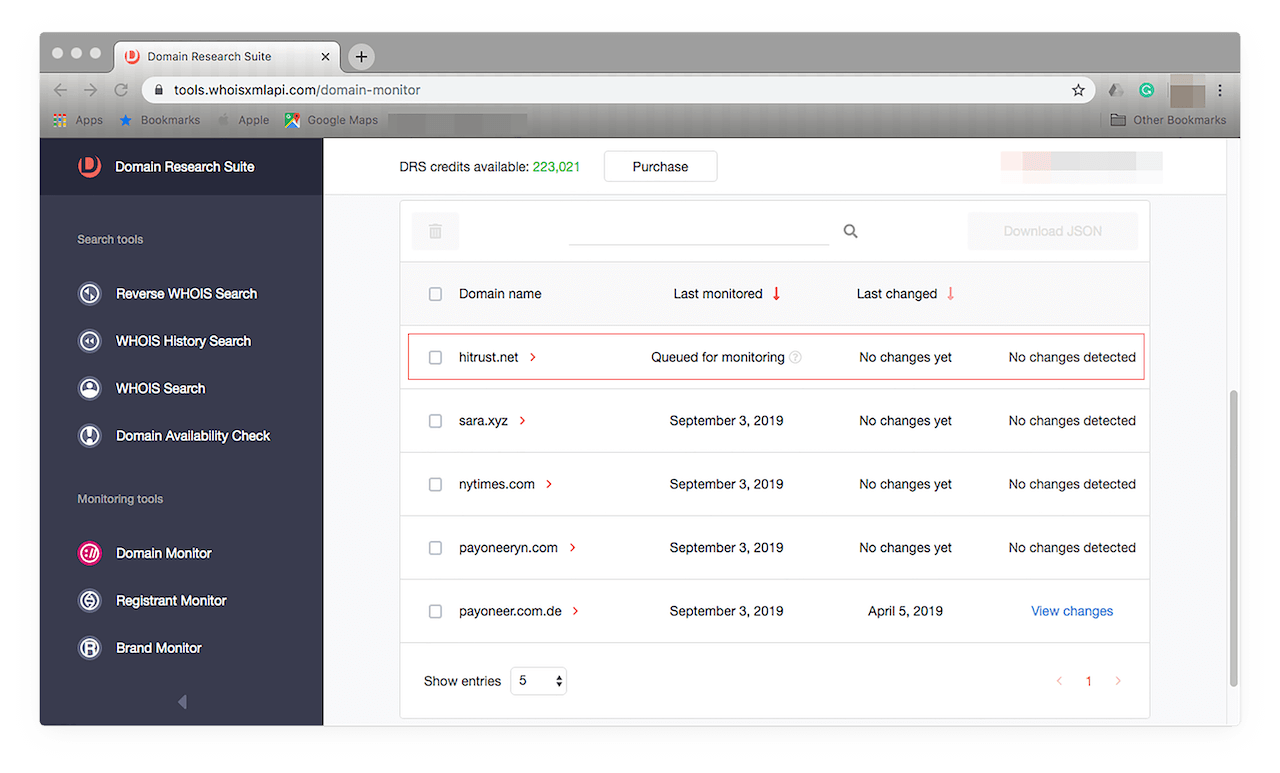
Initial results for this will appear in 24 hours. They should tell you if any changes are detected in the domain’s record.
Registrant Monitor
This tool allows users to keep track of the moves of a particular domain owner. If, say, you suspect a specific registrant of foul play, you can add his name to your tracker. Just access the tool on the menu on the left. That should open this window:
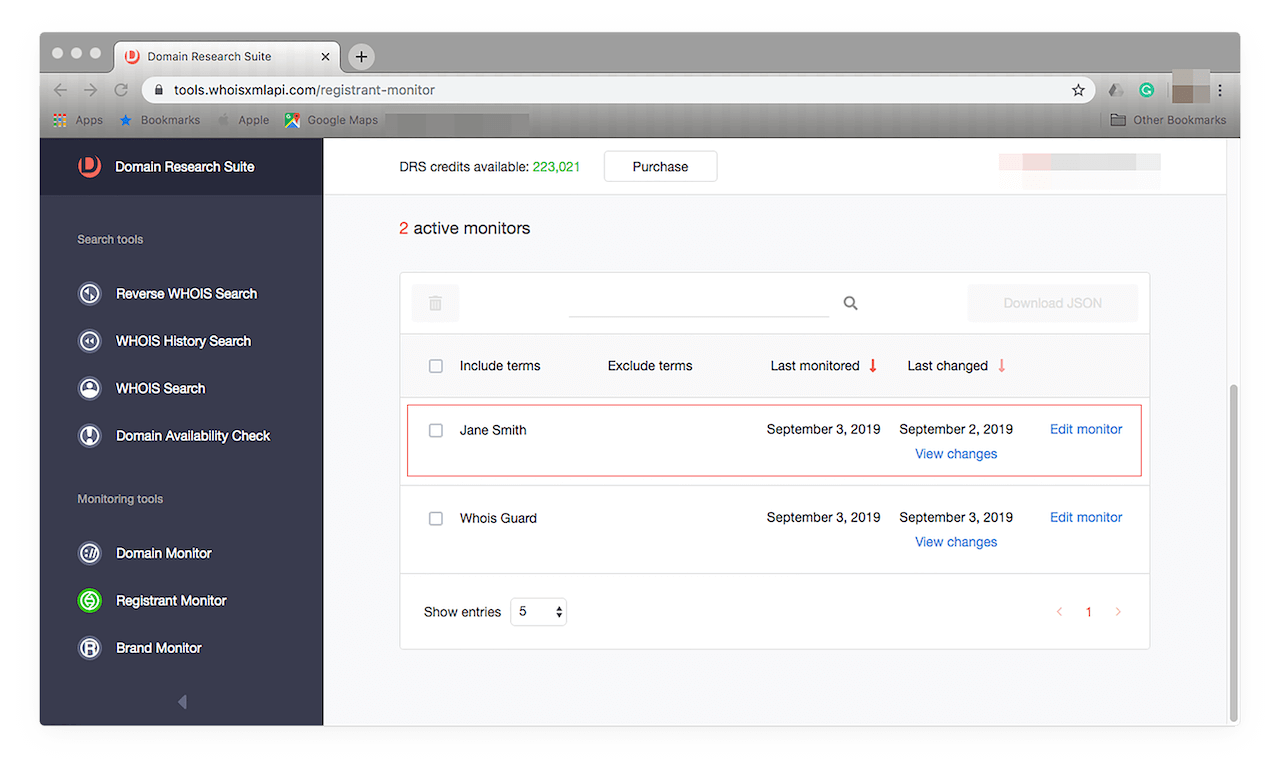
It works in the same way as Domain Monitor. Just type the registrant’s name in the input field and click Add to monitoring. You should see it on your tracker:
The Verdict: Lessons Learned from the Anthem Breach
Many organizations in the healthcare industry have suffered from several kinds of cyber attacks that resulted in serious repercussions. Anthem had to spend millions not only to enhance its existing IT infrastructure but also to pay for damages to those whose personal data was put at risk due to a breach it failed to mitigate. This incident could have caused the organization’s current customers to lose faith in its capability to protect their information. Anthem is, however, fortunate in that it didn’t have to close shop after suffering from the biggest healthcare breach to date.
Some healthcare service providers aren’t that lucky. Smaller entities such as a two-doctor practice in Michigan had no choice but to fold after being affected by an attack. Over the years, hospitals and other healthcare service providers have been cybercriminals’ top-of-mind targets because they are rich sources of personal information. Other reasons include limited cybersecurity budgets, high demand for medical records in black markets, lax bring-your-own-device (BYOD) policies, and employee negligence. As such, many healthcare organizations succumb to ransomware attacks — some have even made the list of top victims such as the Hollywood Presbyterian Medical Center, which paid attackers US$17,000 worth in Bitcoins.
Despite stricter rules and guidelines regarding privacy protection, healthcare organizations continue to suffer from data breaches as well. In the first five months of this year alone, 186 healthcare service providers have reportedly been compromised. These have left the records of more than 6 million patients exposed. The top 10 data breach victims in the healthcare sector for the first half of 2019 include:
- American Medical Collection Agency (AMCA): Exposed the records of 25 million patients; the vendor has since then filed for bankruptcy as investigations pushed on.
- Dominion National: Exposed the records of 2.96 million patients due to unauthorized access.
- Inmedieta Health Group: Exposed the records of 1.5 million patients due to a database misconfiguration.
- UW Medicine: Exposed the records of more than 900,000 patients due to an employee error.
- Wolverine Solutions Group: Exposed the records of around 600,000 patients due to a ransomware attack.
- Oregon Department of Human Services: Exposed the records of 645,000 patients due to a massive phishing campaign.
- Columbia Surgical Specialist of Spokane: Exposed the records of 400,000 patients due to a ransomware attack.
- UConn Health: Exposed the records of more than 300,000 patients after several employees had fallen prey to a spate of phishing attacks.
- Navicent Health: Exposed the records of almost 280,000 patients due to unauthorized third-party access.
- ZOLL Services: Exposed the records of more than 270,000 patients caused by a server migration error.
As evidenced by the list above, phishing remains a concern among healthcare industry professionals. Despite security warnings about the dangers of opening suspicious emails, downloading dubious files, and clicking on unknown links, the healthcare sector remains rife with security’s weakest link — the human factor.
Any company, regardless of the industry, is bound to succumb to a data breach if its employees don’t know how to spot phishing emails. As such, security awareness programs should reiterate telltale signs of phishing emails, which include the use of a public email domain (e.g., gmail.com, etc.), a misspelled domain name (e.g., hitrustaIIiance.net using two capital Is as in igloo instead of two ls as in lion), poorly written content, the inclusion of suspicious-looking attachments or links, and a false sense of urgency (the great bait).
Apart from educating employees, all organizations with an online presence need to protect their assets from all kinds of threats proactively. They can use domain tools, data feeds, and enterprise API packages to check if the users accessing their networks are authorized to do so or if the emails their employees receive are legitimate. This practice is one way to safeguard against data compromise. It can be organizations’ first line of defense against phishing and other attack vectors that ultimately lead to a network breach.
Read other articles







































