CoolWebSearch IoC Investigation Using Maltego
Part 1: CoolWebSearch IoCs
CoolWebSearch is a spyware that has been plaguing Microsoft Windows computers users for more than 10 years now. Owing to the malicious program’s age, more than 50 variants have been discovered so far, all the more widening CoolWebSearch’s coverage.
Our DNS security research team uncovered several CoolWebSearch indicators of compromise (IoCs) and artifacts, which comprise about 200 registrant email addresses and 2,134 domain names. A few of them include:
| IoC registrant email addresses | IoC domain names |
|---|---|
|
|
In this tutorial, we illustrate how these artifacts can be derived via Maltego using WhoisXML API transforms and other WhoisXML API tools.
Note: For complete access to the IoC list analyzed in this post, you can contact us at [email protected] or fill this IoC request form:
Part 2: Obtaining the Registrant Details of a Malicious Domain Name
When investigating a cyber attack, you would want to find out more about all of the cyber resources involved. That would include obtaining the WHOIS records of a suspicious or malicious domain name.
Step 1: We used the transform To WHOIS Records [WhoisXML] on one CoolWebSearch IoC domain flash517[.]com. The transform returned its latest WHOIS record dated 9 July 2021.
We then extracted the registrant email address by running the transform To Registrant Email [WhoisXML].
![We then extracted the registrant email address by running the transform To Registrant Email [WhoisXML]. We then extracted the registrant email address by running the transform To Registrant Email [WhoisXML].](https://main.whoisxmlapi.com/images/solutions/white-papers/coolwebsearch-ioc-investigation-using-maltego/image10.png)
For additional context, we also ran the transforms To Registrant Name [WhoisXML] and To Registrant Organization [WhoisXML]. The latter didn’t return any entity, but we were able to obtain the domain registrant’s name.
![We also ran the transforms To Registrant Name [WhoisXML] and To Registrant Organization [WhoisXML]. We also ran the transforms To Registrant Name [WhoisXML] and To Registrant Organization [WhoisXML].](https://main.whoisxmlapi.com/images/solutions/white-papers/coolwebsearch-ioc-investigation-using-maltego/image16.png)
Part 3: Identifying Connected Domain Names Using a Registrant Email Address
Threat actors may use the same email address to register multiple domain names for their arsenal. As such, it could be worthwhile to obtain a list of domain names that contain the suspicious or malicious email address in their current and historical WHOIS records.
We looked into the registrant email addresses known for being used in registering domain names involved in the CoolWebSearch campaigns. There are hundreds of them, so we handpicked a few.
Step 1: On Maltego, add an “Email Address” entity from the “Personal” category on the Entity Palette on the left side of your screen. The entity categories are arranged alphabetically, so you may need to scroll all the way down.
We then added three email addresses related to CoolWebSearch.

Step 2: We ran the transform To Domains and IP Addresses (Historical Reverse WHOIS Records Search) [WhoisXML] on each email address. This process returned domain names that contain the email address in their historical WHOIS records.
What does this mean? At one point in these domains’ existence, they may have served CoolWebSearch malware. Here are the results for each email address.
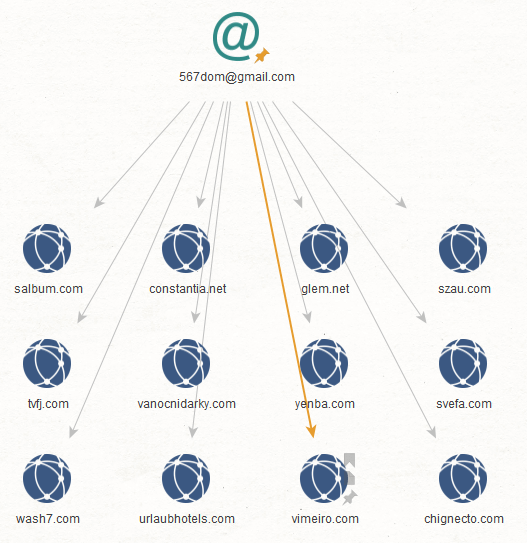
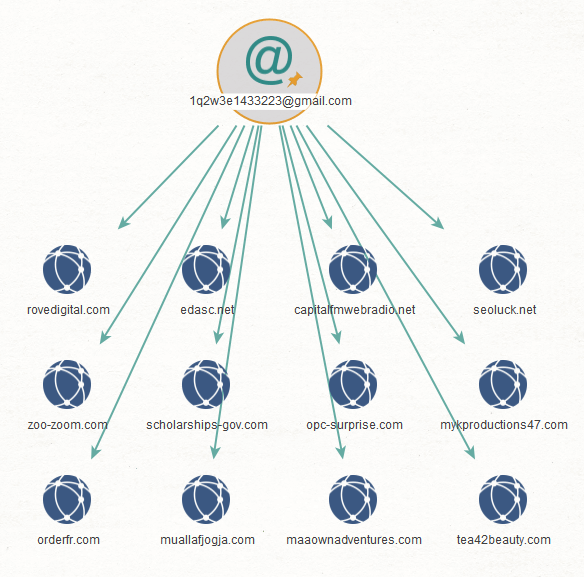
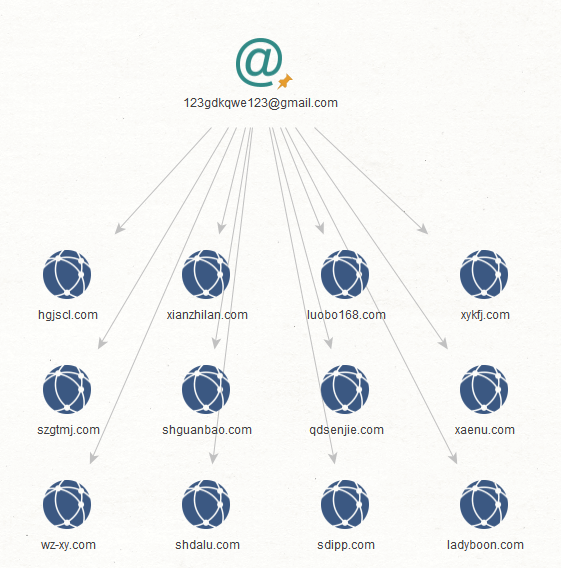
Step 3: How about domain names that use the same email address in their current WHOIS records? That would tell us that the registrant is the most recent owner of the domain. To find out, we ran the transform To Domains and IP Addresses (Reverse WHOIS Records Search) [WhoisXML] on each email address.
Remember that in step 2, we looked into historical WHOIS records and used the transform To Domains and IP Addresses (Historical Reverse WHOIS Records Search) [WhoisXML].
Below are some of the connected domains whose latest WHOIS records contain the email addresses:
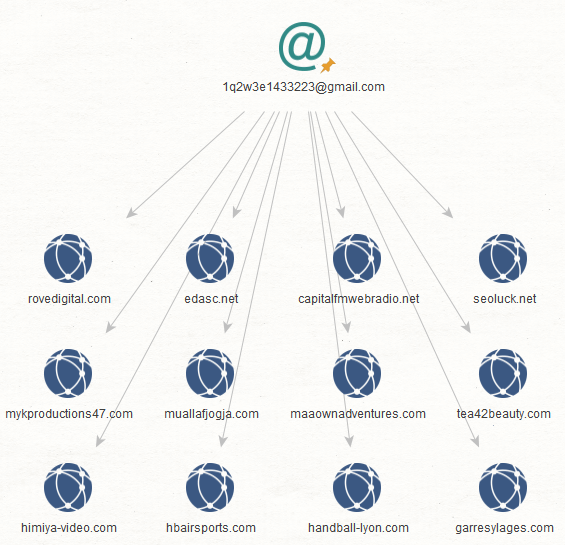
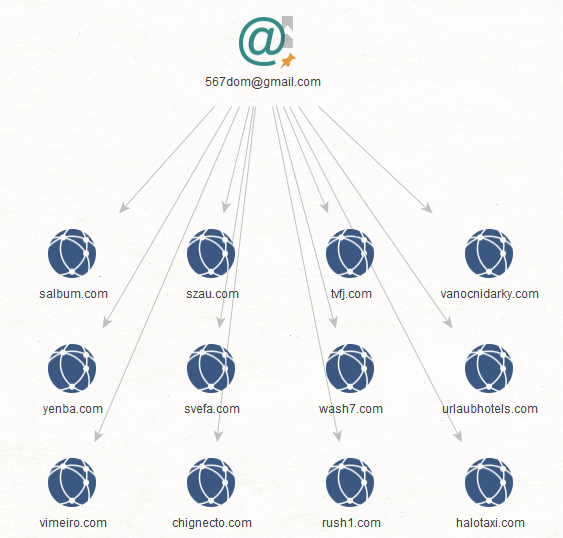
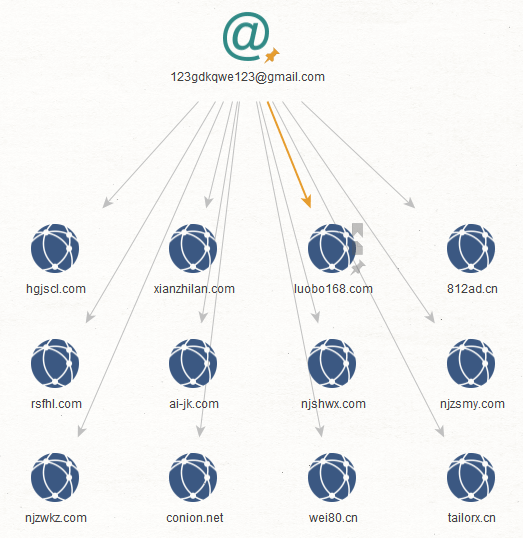
Some domain names may also be present in the historical WHOIS record search results (in step 2).
Step 4: Part of the investigation could include determining the type of content these malware-serving domains currently host or hosted in the past. The transform To Snapshots [Wayback Machine] can make it easier to determine which domains have existing snapshots.
We ran the said transform on three different domains—scholarships-gov[.]com, zoo-zoom[.]com, and ladyboon[.]com. We then retrieved a sample snapshot from the Wayback Machine for each domain.
From these screenshots, we can determine that the threat actors behind CoolWebSearch do not necessarily have a specific target or phishing technique in mind. They tend to spread out their attack vectors to involve multiple website categories, thereby targeting several niches.
Check out the images below for reference.
scholarships-gov[.]com
![scholarships-gov[.]com scholarships-gov[.]com](https://main.whoisxmlapi.com/images/solutions/white-papers/coolwebsearch-ioc-investigation-using-maltego/image19.png)
![scholarships-gov[.]com scholarships-gov[.]com](https://main.whoisxmlapi.com/images/solutions/white-papers/coolwebsearch-ioc-investigation-using-maltego/image7.png)
zoo-zoom[.]com
![zoo-zoom[.]com zoo-zoom[.]com](https://main.whoisxmlapi.com/images/solutions/white-papers/coolwebsearch-ioc-investigation-using-maltego/image21.png)
![zoo-zoom[.]com zoo-zoom[.]com](https://main.whoisxmlapi.com/images/solutions/white-papers/coolwebsearch-ioc-investigation-using-maltego/image1.png)
ladyboon[.]com
![ladyboon[.]com ladyboon[.]com](https://main.whoisxmlapi.com/images/solutions/white-papers/coolwebsearch-ioc-investigation-using-maltego/image9.png)
![ladyboon[.]com ladyboon[.]com](https://main.whoisxmlapi.com/images/solutions/white-papers/coolwebsearch-ioc-investigation-using-maltego/image14.png)
Part 4: Obtaining More Details Related to an Email Address
Aside from domain name registrations, you can also use email addresses when signing up for accounts and leaving comments on blogs and websites. You would want to find out everything you can about an email address that is dubbed “malicious.”
To illustrate how Maltego can help you with this objective, we used 53680327@qq[.]com as a starting point. This email address was used to register domains serving CoolWebSearch malware.
Step 1: Use the transform To Website [using Search Engine] to see websites that mention the email address. This information allows you to get a glimpse of the email address’s footprint on the Internet.
![Use the transform To Website [using Search Engine] to see websites that mention the email address. Use the transform To Website [using Search Engine] to see websites that mention the email address.](https://main.whoisxmlapi.com/images/solutions/white-papers/coolwebsearch-ioc-investigation-using-maltego/image4.png)
Part 5: Identifying IP Address Resolutions and Uncovering Connected Domains
Now that we have demonstrated how to go about identifying WHOIS registration records and obtaining domain names that share the same registrant email address, we move on to obtaining connected domains that share the same IP address with a suspicious or malicious domain.
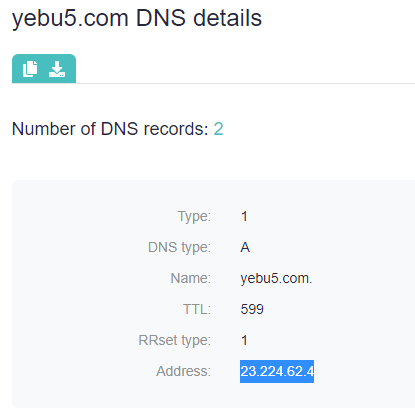
Step 1: At this point, we used DNS Lookup to identify the IP addresses of one of the CoolWebSearch domains, yebu5[.]com resolves or resolved to in the past. We identified one IP address—23[.]224[.]62[.]4.
Step 2: On Maltego, we added an IPv4 Address entity for the IP address obtained from DNS Lookup. We then ran the transform To WHOIS Records [WhoisXML], which returned records dated 22 November 2016.
From there, we ran the transform To Registrar [WhoisXML] to determine the organization that has control over the IP address. The registrar can help with the takedown process of the IP address and the domains associated with it. For our sample, that would be the American Registry for Internet Numbers (ARIN).
![We ran the transform To Registrar [WhoisXML] to determine the organization that has control over the IP address We ran the transform To Registrar [WhoisXML] to determine the organization that has control over the IP address](https://main.whoisxmlapi.com/images/solutions/white-papers/coolwebsearch-ioc-investigation-using-maltego/image3.png)
Step 3: Domain names that share the same IP address can be considered artifacts, especially when dealing with dedicated IP addresses. We used Reverse DNS Search to uncover 162 artifacts related to 23[.]224[.]62[.]4.
![We used Reverse DNS Search to uncover 162 artifacts related to 23[.]224[.]62[.]4. We used Reverse DNS Search to uncover 162 artifacts related to 23[.]224[.]62[.]4.](https://main.whoisxmlapi.com/images/solutions/white-papers/coolwebsearch-ioc-investigation-using-maltego/image12.png)
Conclusion
We learned from this investigation that the actors behind the CoolWebSearch malware seem to use different types of domain names and websites. Some domain IoCs appear to have been randomly generated, while others contain decipherable words. The websites, on the other hand, host different kinds of content, a tactic that widens the attack’s scope, which could be one of the reasons why the malware is still alive.
Uncovering CoolWebSearch IoCs and artifacts can help security teams protect users. Determining their registrant and registrar details can also help facilitate the reporting and takedown processes. Furthermore, the IoCs and artifacts identified can be expanded by looking at the connected domains based on IP address resolutions.
For complete access to the IoC list analyzed in this post, you can contact us at [email protected] or fill this IoC request form.
Read other articles


































