How Domain Data Can Help Law Enforcement Agencies Nab a Cybercriminal Gang Mastermind: The Business Club Case

It’s no secret that Cybercriminal operations are not very different from how legitimate businesses operate. Much like a CEO heads a global corporation, a mastermind may stand behind the most notorious and widespread cybercriminal gang.
In the early 2000s, the most prominent cybercriminal rings had a mafia-like structure as they were led by the so-called “dons”. Each don had a right-hand man known as a “consiglieri,” who made sure the wheels of the operation kept turning.
The very first cybercriminal gangs that gained notoriety for reaping millions of dollars from victims the world over while evading capture for years include CarderPlanet, Shadowcrew, and the RBS WorldPay Gang. Times may have changed, and the rings’ structure, tools, tactics, and targets may no longer follow those of the old crews, but cybercriminal attacks continue to linger on. Though we still see reports on the misdeeds of individual threat actors today, cybercriminal rings continue to wreak greater havoc due to the scale of their operations — the case in point: The Business Club.
This downloadable white paper will take a closer look at the Club in action and show how domain intelligence feeds and APIs could help in similar situations.
Table of contents
- The Attack: The Business Club in Action
- The Case Facts: Behind the Operation
- A Possible Solution: Can Domain Data Help the Good Guys?
- The Verdict: Lessons Learned from the Business Club Case
The Attack: The Business Club in Action
The Business Club is a notorious Eastern European organized cybercriminal gang accused of stealing more than $100 million from banks and businesses worldwide. Apart from pulling off profitable heists, it was also believed to have ties with phantom Chinese firms conducting cyber espionage in the region of Russia’s far eastern border.
The Victims
Members of the Business Club are known to have preyed on banks and small businesses. Believed to have been operating since as early as 2011, around six core group members supported by some 50 individuals who acted in capacities, including 24 x 7 tech support technicians, third-party malware suppliers, and money mules, emptied the bank accounts of victims from China, Australia, the U.S., and other parts of the world.
The Attack Vector
The Business Club’s successful operations relied on scare tactics to trick victims into paying up. How did they deliver their nasty payloads to the victims’ computers? By the oldest but still effective means — email.
The Bait
One of the ruses the Business Club members used to reel in targets were legal threats delivered via email with malware-laced attachments. In this particular case, the malicious attachments came in the form of Microsoft Word documents that supposedly contained details on a suit filed against the victim. Of course, anyone scared enough ended up opening the attachment, infecting his computer with the perpetrator’s malware of choice. In this case, the gang used tools from the GameOver ZeuS arsenal.
The Case Facts: Behind the Operation
The Business Club is believed to be led by Evgeniy Mikhailovich Bogachev (most popularly known in the cybercriminal underground as “Slavik”), the alleged creator of the GameOver ZeuS malware, who in 2018 joined the Federal Bureau of Investigation (FBI)’s most wanted list with a $3-million bounty on his head.
Cybercriminals who wish to become part of the Business Club have to pay an initial membership fee. With that came a profit-sharing agreement. They did not reap the full benefits of membership, however, until they prove themselves worthy — a typical practice in the cybercriminal underground known as “vetting.” In-depth research revealed that the gang’s members covered Russia’s 11 time zones, allowing them to pull off cyber heists in any part of the world.
Business Club members had access to the GameOver ZeuS botnet panel (dubbed the “World Bank Center” with the tagline “We are playing with your banks”), so they can hijack victims’ online banking transactions. The tool also enabled them to bypass security features, including the use of one-time tokens and secret questions. It looked like this:
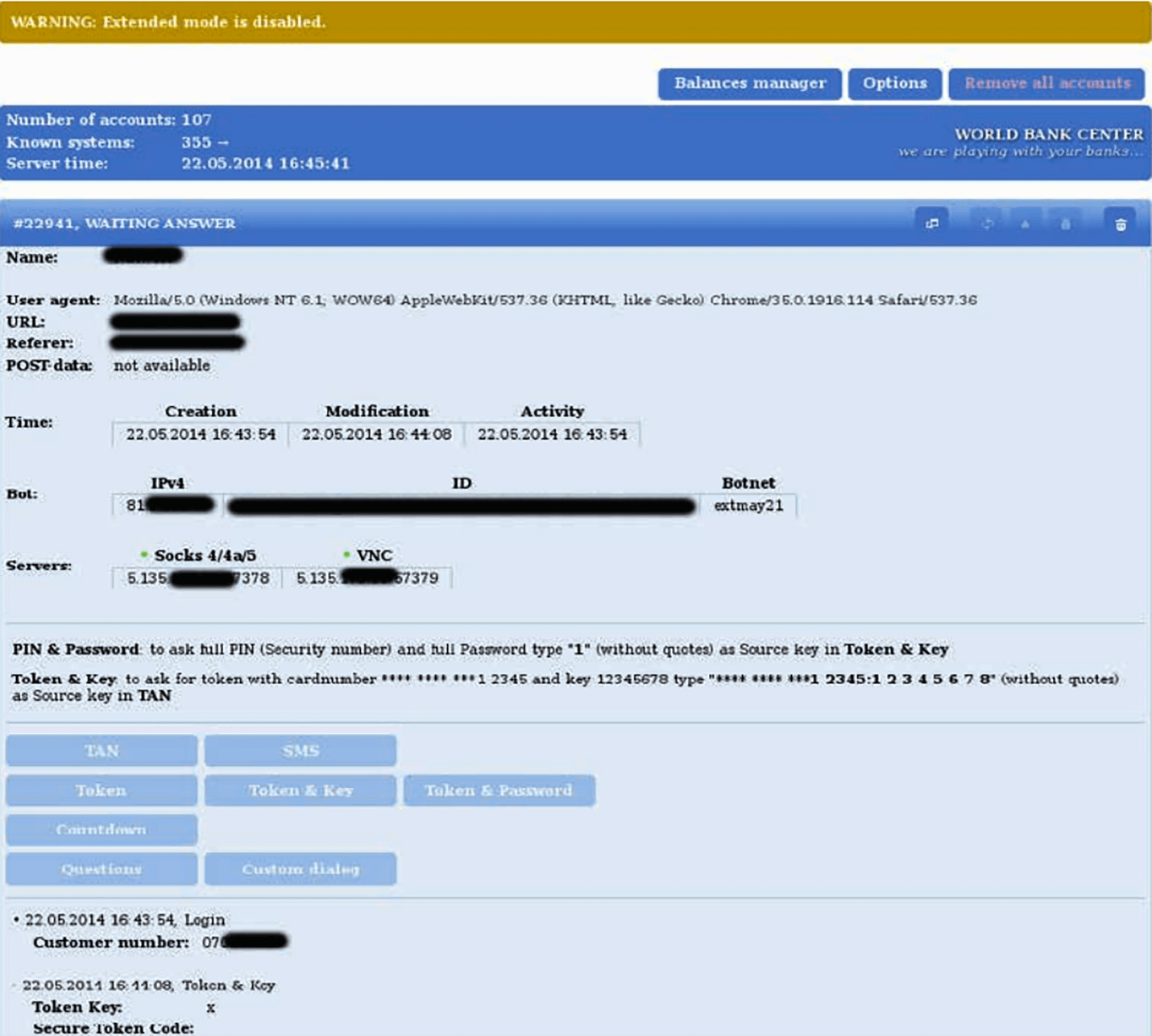
Once the victim’s account has been compromised, the cybercriminal can quickly initiate a fund transfer (at most times, the entire balance) from the target’s to the group’s own account. Moreover, because he used the account owner’s credentials and managed to bypass even the additional layers of security without a hitch, the bank would approve the transaction unless the account owner is alerted beforehand and thus stops the transfer from happening. That didn’t often seem to be the case, however, as evidenced by the gang’s recorded earnings.
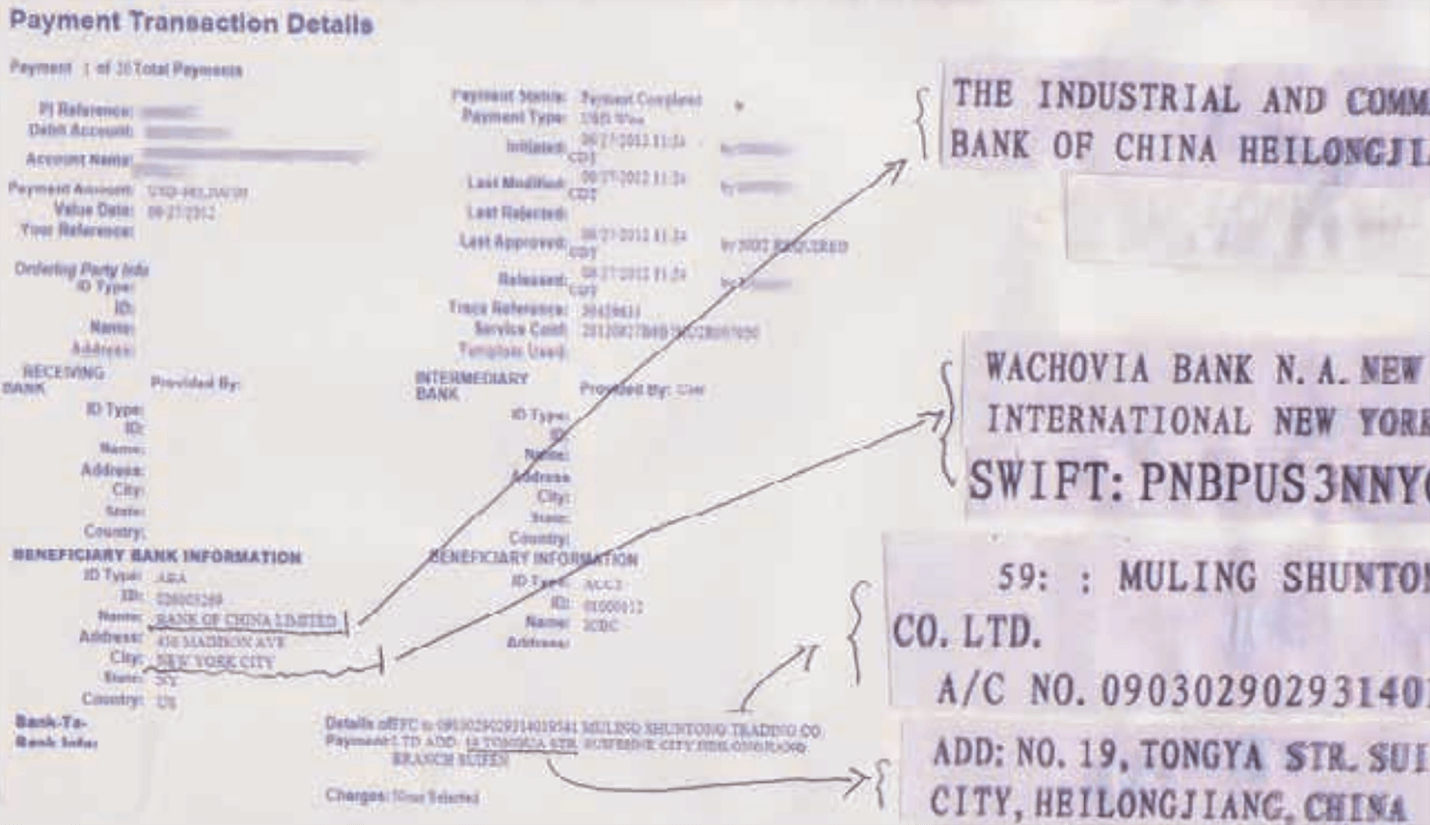
According to an FBI alert issued on April 2011, following the loss of $20 million from various small businesses in the U.S., members of the Business Club siphoned off victims’ bank balances to accounts of bogus Chinese firms (their money mules) located on or near the country’s border with Russia. See a sample bank transfer from a victim in the U.S. to a fake Chinese firm below.
After years of gathering information on similar attacks, Fox-IT researchers managed to gain access to a Business Club server that allowed them to identify the mind behind the global cybercrime ring — Evgeniy Mikhailovich Bogachev, more popularly known by his aliases as “Slavik,” “lucky12345,” and “Pollingsoon.” Not only is he wanted for conspiracy to participate in racketeering activity, bank fraud, conspiracy to violate the Computer Fraud and Abuse Act, conspiracy to violate the Identity Theft and Assumption Deterrence Act, aggravated identity theft, conspiracy, computer fraud, wire fraud, money laundering, and conspiracy to commit bank fraud, but he is also suspected of cyber espionage targeting Russia’s neighbors that include Georgia, Turkey, and Ukraine. No evidence of the rest of the Business Club members’ involvement in this, however, has been found.

A Possible Solution: Can Domain Data Help the Good Guys?
Catching thieves in the real world is challenging enough but doing so online is even harder. Today’s cybercriminals come armed with all the bells and whistles to stay under the authorities’ radars. As a result, law enforcement agents need to keep up with the latest in technology and learn how to use it to catch cybercriminals.
As in real-world heists, cyber thieves can leave traces though these may not be as easy to pick up. Law enforcement agents on their trail need at least a domain, an IP address, or an email address before they can even start connecting the dots and pinpointing perpetrators who typically only go by on aliases.
In the Business Club’s case, the FBI got the most significant lead when Fox-IT researchers managed to infiltrate one of the gang’s command-and-control (C&C) servers. As you would probably know by now, every server or system, in general, has its own IP address.
Given that, a law enforcement agent hot on the Business Club’s trail can use domain data to obtain as much publicly available information on the server as possible. Let’s take a closer look at what WHOIS information can give us and how this can aid in similar investigations via the following step-by-step guide:
- 1. Visit https://whoisapi.whoisxmlapi.com/ and scroll down until you see “Give the API a Try” where you
can enter an IP address.
![Visit https://whoisapi.whoisxmlapi.com/ and scroll down until you see “Give the API a Try” where you can enter an IP address. Visit https://whoisapi.whoisxmlapi.com/ and scroll down until you see “Give the API a Try” where you can enter an IP address.]()
- 2. Because publicly available reports on the Business Club case do not contain domain information, we used an IP address (i.e., 176.8.154.150) related to a GameOver ZeuS attack that may not necessarily have ties to the gang in question.
- 3. You can get results in both the XML or JSON format. The results in XML format would look like this:
In JSON format, you should see something like this:
![You can get results in both the XML or JSON format. You can get results in both the XML or JSON format.]() Regardless of which format you choose, you should see when the domain was created and last updated, who its registrant is (including his organization, physical and email addresses, and phone number), all other IP addresses related to it, relevant contacts and their details, and other information. If none of the raw formats work for you, hit the Preview button so you can see the results in formatted text, which looks like this:
Regardless of which format you choose, you should see when the domain was created and last updated, who its registrant is (including his organization, physical and email addresses, and phone number), all other IP addresses related to it, relevant contacts and their details, and other information. If none of the raw formats work for you, hit the Preview button so you can see the results in formatted text, which looks like this:![In JSON format, you should see something like this In JSON format, you should see something like this]()
![Hit the Preview button so you can see the results in formatted text, which looks. Hit the Preview button so you can see the results in formatted text, which looks.]()
- 4. Investigators can take note of all related domains and/or IP addresses and check each one for ties to
malicious activities. They can then advise users to block access to these sites for their protection via
security bulletins. They can also take note of the organizations, individuals, and email addresses tied
to the domains and/or IP addresses in question for further investigation. All of the information
available in a domain database can serve as leads for law enforcement agents who are going after
suspects.
![Investigators can take note of all related domains and/or IP addresses. Investigators can take note of all related domains and/or IP addresses]()
- 5. Given the name of the organization that owns the domain or IP address, a simple Web search can point
investigators to a website that could give more information. Note, however, that cybercriminals are
known to compromise the sites of legitimate businesses and use these for malicious purposes. That said,
before deciding to block access to an entire IP block as in Kyivstar’s case, first make sure that it is
guilty of the crime.
![Given the name of the organization that owns the domain or IP address Given the name of the organization that owns the domain or IP address]()
- 6. As it turns out, Kyivstar is indeed a Ukrainian telecommunications company that has been operating
since 1994. Contact the organization and let it know what’s going on. It may not be aware that
cybercriminals are abusing its online property. Asking questions such as whether it has been receiving
customer complaints about suspicious activities or billing complaints would be an excellent first step
as these could be indicators that the organization’s security has been breached.
Note that in many cases, cyber attackers would hide behind the IP addresses of service providers to
evade detection and blocking. That could very well be why Kyivstar’s IP address figured into the case.
![As it turns out, Kyivstar is indeed a Ukrainian telecommunications company that has been operating since 1994. As it turns out, Kyivstar is indeed a Ukrainian telecommunications company that has been operating since 1994.]()
- 7. If the company has been receiving complaints, ask for details. If it kept emails and other digital evidence of these, ask for copies. These could provide more bread crumbs (email addresses, mail servers, contact details, etc.) that you can pursue.
- 8. Validate the veracity of each WHOIS record’s contents before making accusations of foul play. This step is tedious but, unfortunately, necessary in any criminal investigation. A party’s guilt needs to be proven first even before a case can be filed in a court. Make comparisons and connections to determine the root source of a threat or in the Business Club’s case, its mastermind.
- 9. Throughout your investigation, you’re bound to come across the following information from WHOIS API
results that can serve as leads:
- a. Estimated domain age: Cybercriminals don’t hold on to domains for very long periods. This tactic allows them to evade discovery. So, relatively new domains should come under suspicion.
- b. Contrasting information: Cyber attackers are bound to use personal (e.g., gmail, etc.) rather than corporate email addresses in contact details. It is, after all, easier to create a free email account than to set up a fake corporate account. Note, however, that an organization’s contact person for domain-related concerns is more likely to use his or her corporate email address. Quick Web searches to compare the company information (physical address, phone number, domain, etc.) in a registrant’s WHOIS record with the contact details on that organization’s website can also reveal suspicious intentions. Look out for misspellings in the domain name as well. You could be dealing with a phisher or criminal in the guise of an employee of a legitimate organization that ought to get your attention.
- c. Incomplete data: Cybercriminals typically limit the amount of information they reveal about their identities. Though registrants can legally opt for anonymous or private domain registration, most still complete their records using the registrar’s contact details. Make sure the registrar details match those of the registrant’s in such cases.
- 10. Despite the wealth of information that can be obtained from a WHOIS API, however, you may still fall
short on actionable intelligence. It would thus be a good idea to download a WHOIS database. A reliable
database for domain-led investigations provides information that can help you connect the dots, so to
speak, when going after a cybercriminal gang. Unlike a WHOIS API, however, having a database on hand can
let you find similarities between domains, registrants, email addresses, and several details. Take a
closer look at a sample WHOIS database below.
![It would thus be a good idea to download a WHOIS database. It would thus be a good idea to download a WHOIS database.]()
- 11. If you’re going after not just an individual but a group of criminals, then, you can sort the
information in the database alphabetically, for instance, to make connections. That said, if you have an
email address used for the attack, you can sort the entries in the database by contactEmail. All of the
domains with that email address can then be identified for a deeper dive. The same process can be
applied to the following fields:
- a. Domain name
- b. Name servers
- c. Date created
- d. Date last updated
- e. Expiration date
- f. Status
- g. Registrant’s name, email address, organization, physical address, and phone and fax numbers
- h. Administrative contact’s name, email address, organization, physical address, and phone and fax numbers
- a. The same domain name can point you to the cyber attacker’s network. A gang could have purchased a domain for a series of attacks targeting several individuals or businesses. You could thus uncover an ongoing massive campaign.
- b. Similarities in name servers could lead you to discovering a gang’s C&C servers. If you manage to do that, you would fundamentally have broken the case wide open. A C&C server can help you determine what tools the attackers used, what vectors they abused, who their targets were, who the members of their crime ring are, etc.
- c. Short-lived domains, as has been pointed out earlier, are at the core of a cyber attack. Compare creation and expiration dates. Are any of them too similar for a mere coincidence? Check out the domains’ status as well. Law-abiding citizens most likely own those that are kept by the registrant indefinitely (indicated by a status like "clientDeleteProhibited -- http://www.icann.org/epp#clientDeleteProhibited|clientRenewProhibited -- http://www.icann.org/epp#clientRenewProhibited|clientTransferProhibited -- http://www.icann.org/epp#clientTransferProhibited|clientUpdateProhibited -- http://www.icann.org/epp#clientUpdateProhibited"). Remember that cybercriminals don’t typically hold on to domains. They change domains on the fly to evade detection and capture.
- d. Look closely at update dates. Compare these with external findings on changes to known criminal modus operandi. You could uncover cases that are related to one another in this manner.
- e. Though cyber attackers typically use aliases, they could be using just one or a few in several attacks. Like regular businesses, after all, cybercrime gangs and their masterminds have a reputation (although a seeming one) to maintain. So, spot similarities in registrant and administrative contact names. Who knows? You may end up catching a well-known cybercrime mastermind behind it.
- 12. Setting up a local WHOIS database in ElasticSearch using WhoDAT can also enable more advanced searches. Using statistical and machine learning (ML) approaches can also help. Applying these techniques, the WHOIS database can identify domain networks which are likely to belong to a particular cybercriminal gang.
- 13. Users who wish to find out if domains have been involved in previous misdeeds can also look into historical WHOIS data via WHOIS History API.
The Verdict: Lessons Learned from the Business Club Case
Criminal investigations always require forensic evidence before a case can be filed in any court of law. Much like pursuing suspects in the physical world, cybercriminal investigations require specific steps to follow, namely:
- Assess the situation: A law enforcement agent must first determine specific crime elements and if the laws in his jurisdiction support prosecution. He must be sure that the charges stick if guilt is proven. The technology used may not yet be covered by existing laws. Most digital crimes are global in nature and so making sure your jurisdiction covers them is critical.
- Conduct an initial investigation: Ask who, what, where, when, why, and how questions, along with:
- Who are the potential suspects?
- What crimes were committed?
- When were the crimes committed?
- Were these crimes limited to a particular jurisdiction?
- What kind of evidence can be collected?
- Where could physical and digital evidence be found?
- What types of physical and digital evidence were used in the crime?
- Does any of the evidence need to be immediately preserved?
- How can the evidence be preserved and maintained for court proceedings?
- Identify possible evidence: Digital evidence can come in many file types and sizes. They may also be encrypted, protected, or otherwise hidden. If your agency does not have the resources, tools, or specific expertise necessary to identify and collect these, consider partnering with other parties that have the required capabilities.
- Secure devices and obtain court orders: In many cases, investigators may seize electronic devices without a warrant but must obtain one to go through them. Multiple warrants may need to be obtained if a particular device is connected to several crimes. These should clearly describe all files, data, and electronic devices to be searched as precisely as possible and seek approval to perform analysis offsite such as in a specialized cyber-forensic laboratory. Subpoenas can also be used to obtain digital evidence. Security and other private organizations may be tapped to assist in law enforcement cases. Nondisclosure agreements (NDAs) may also be needed if the agency does not want the suspect’s electronic service provider (ESP) to notify the target of the ongoing investigation. Court orders are also required to compel ESPs to give out information on their clients.
- Analyze results with the prosecutor: Work with the prosecutor to identify the appropriate charges and determine what additional information or evidence is needed before filing charges.
You may have noticed how laborious the steps in conducting a cybercriminal investigation are. The hardest step is acquiring enough bulletproof evidence to file a case against perpetrators who bask in the anonymity that the virtual world generously offers. With the right domain tools, data feeds, and enterprise API packages that help identify potential suspects and pinpoint their origins though, law enforcement agents can get more solid leads and evidence that will ultimately help them solve cases.
Domain research and monitoring tools such as Domain Research Suite should also be part and parcel of a law enforcement agent’s arsenal. With it, agents can perform various actions that can spell the difference between catching the bad guys or letting them get away. Even with just a company name, a phone number, or an email address, for instance, they can launch basic, reverse, and historical WHOIS searches that will provide accurate and timely information on potential suspects. Constant monitoring of domains, brands, and registrants tied to attacks and criminals is also possible with such a tool.
If you’re interested in pursuing a career in law enforcement or are already an officer who has run out of leads for an ongoing investigation, you may wish to try our tools out. Sign up for free and see if they help.
Read other articles










































