How to use WHOIS XML API in Combination with Maltego for Advanced Bulletproof Malicious Infrastructure Investigation
Table of contents
- Executive Summary
- Introduction to WHOIS XML API
- How to get a proper account
- How to install Maltego
- How to use the WHOIS XML API Maltego Integration
- Profiling a Bulletproof Hosting Infrastructure - A Case Study
- Basic OSINT Enrichment Process
- Conclusion
Executive Summary
The cybercrime ecosystem is dominated by thousands of daily fraudulent releases that also include modular and open-source malware and rapidly developing DIY (do-it-yourself) malware-generating kits, including cybercrime-as-a-service type of underground market fraudulent propositions. It shouldn’t be surprising that among the key driving forces behind the rise of today’s modern cybercrime ecosystem remains the bulletproof hosting provider infrastructure which basically allows novice and experienced cybercriminals to host their malicious releases such as malware, spam, and phishing campaigns online for as long as possible. All of this is done largely thanks to a growing trend and the rise of bulletproof hosting providers, which basically offer advanced and sophisticated hosting services for cybercriminals and their releases, potentially increasing the average online time for a fraudulent and malicious campaign for the purpose of improving its QA (Quality Assurance) and making it harder for the good guys to take it offline. This, in turn, could cause financial loss and actual campaign shutdown activity and downtime for the bad guys to deal with.
Thanks to the modern and vast infrastructure of WhoisXML API and its billions of IP and domain records, including historical and current WHOIS records, it’s becoming increasingly easy for novice and experienced cybercrime researchers, investigators, and threat intelligence analysts to map and respond to modern cyberattack and cybercrime trends. Bulletproof hosting providers also aim to map their infrastructure while looking for personally identifiable information and leads, in terms of cyberattack and cyber campaign attribution as well as also attempting to take down and offline a rogue and bulletproof hosting provider’s infrastructure. Doing that may potentially cause widespread damage and financial loss for the bad guys and potentially disrupt their malicious and fraudulent activities online.
In this article we’ll discuss the use of Maltego in combination with WhoisXML API for the purpose of mapping and exposing a currently active bulletproof hosting provider. We’ll use a variety of means and techniques, potentially attempting to build a working case and actually to try and take it offline in addition to actually revealing currently active fraudulent and malicious Web sites hosted on the bulletproof hosting provider’s infrastructure including to present an OSINT research and enrichment case study on one of the websites which we found on the bulletproof hosting provider’s infrastructure, which is basically a high-profile online E-shop offering access to stolen credit cards.
Introduction to WHOIS XML API
WhoisXML API is one of the Web’s and the security industry’s primary destinations for threat intelligence and cybercrime research, including OSINT types of domain, IP, and current and historical WHOIS data records with billions of domain, IP, and WHOIS records within WhoisXML API’s database. Novice and experienced cybercrime researchers and threat intelligence analysts, including OSINT experts and analysts, should consider adopting WhoisXML API’s products in their arsenal of OSINT tools and public database repositories and databases, particularly considering the tools offered as their primary information sources and threat intelligence gathering solutions and publicly accessible databases for using them in their current and ongoing OSINT and cybercrime analyses including threat intelligence type of investigations.
How to get a proper account
Cybercrime researchers and threat intelligence analysts interested in obtaining access to one of the Web’s and the industry’s most comprehensive and in-depth data set of real-time and historical domain IP and WHOIS information should grab an account from the following URL - https://main.whoisxmlapi.com/signup in order to begin their OSINT and cybercrime research including their threat hunting and threat intelligence gathering process.
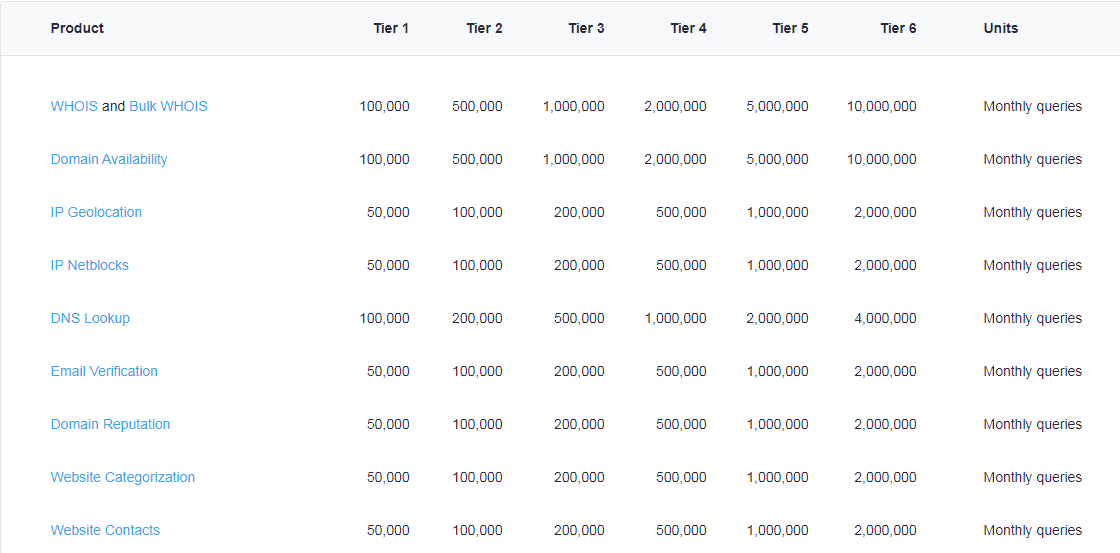
Sample WhoisXML API Pricing Plans Web Site
How to install Maltego
For the purpose of this case study we’ll use the popular OSINT gathering and enrichment tool Maltego, which you can grab from the following URL - https://www.maltego.com/downloads/ to begin using and utilizing WhoisXML API’s advanced domain, IP, and historical and current WHOIS information and one of the Web’s and the industry’s most comprehensive and in-depth databases.
Sample Maltego Download Web Site
How to use the WHOIS XML API Maltego Integration
Before using Maltego users should follow the instructions and grab a proper WhoisXML API account which they can later on use for the actual research and OSINT research and analysis, including the actual enrichment process.
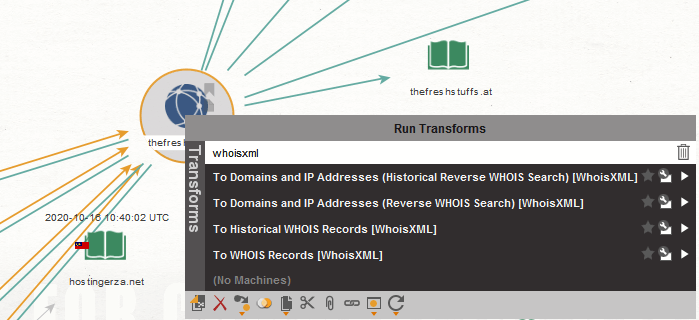
Sample Maltego GUI Interface relying on WHOIS XML API’s for OSINT research and analysis and actual network and domain reconnaissance and footprint including actual enrichment
Users then need to proceed with the actual OSINT research and enrichment process by importing the domains and actual IPs for their research in questions directly into Maltego, either by using the import feature or by manually adding them for the purpose of actually beginning the actual OSINT enrichment and research process.
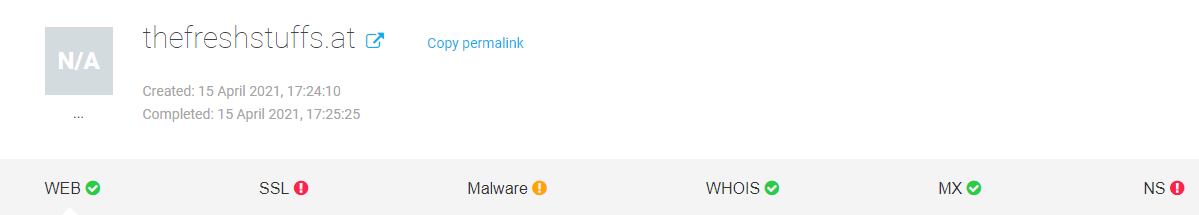
Sample WHOIS XML API Report for a Sample Stolen Credit Cards Selling E-Shop Found Within the Hosting Infrastructure of the Bulletproof Hosting Provider

Sample Related Domains Found Within the Bulletproof Infrastructure Provider’s Hosting Infrastructure Revealed and Exposed via WHOIS XML API’s Database
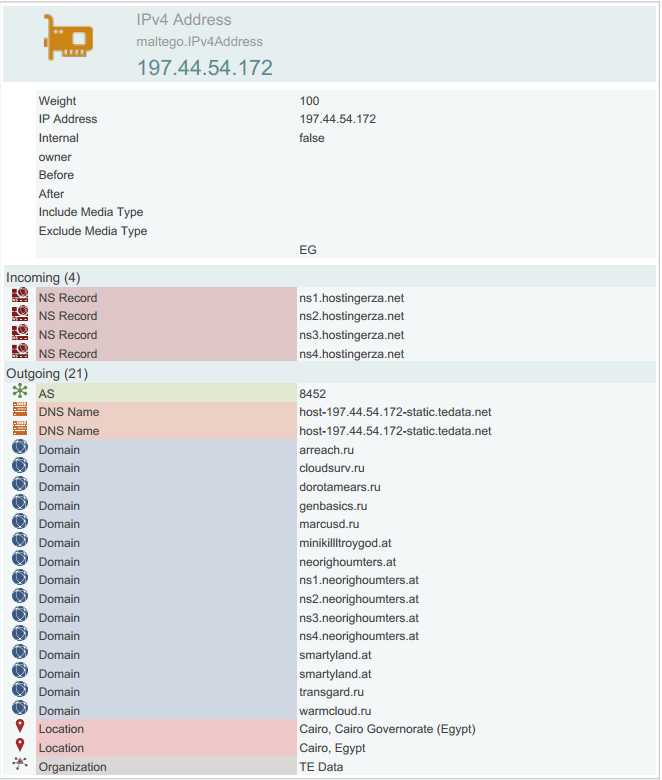
Sample Bulletproof Hosting Provider’s IP Profiled and Exposed via WHOIS XML API’s Database
Profiling a Bulletproof Hosting Infrastructure - A Case Study
For the purpose of this case study, we’ll profile and expose a currently active bulletproof hosting infrastructure provider and use a sample E-shop for stolen credit cards data as an example, including in-depth and practical OSINT research and enrichment advice in the process of exposing the bulletproof hosting infrastructure provider and the actual E-shop for stolen credit cards - hxxp://thefreshstuffs.at.
Thanks to the vast and comprehensive WhoisXML API database, we’ve managed to successfully profile and map the bulletproof hosting provider’s infrastructure exposing related malicious and fraudulent domains hosted on the same bulletproof hosting provider’s infrastructure, which also includes a currently active E-shop for stolen credit cards information.
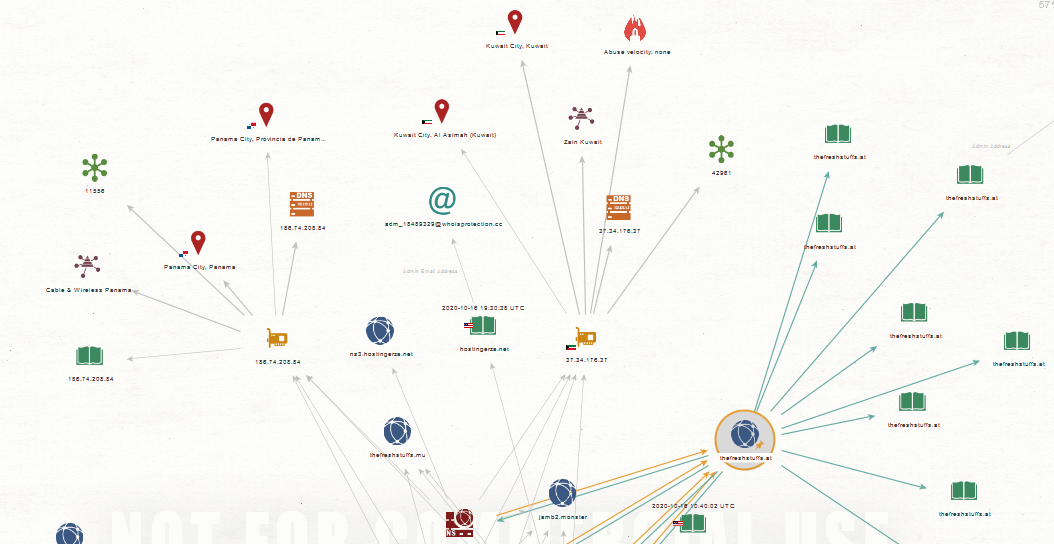
Sample Maltego GUI Graph relying on actionable threat intelligence on the bulletproof hosting infrastructure produced by WHOIS XML API’s database
Basic OSINT Enrichment Process
The E-shop in question (hxxp://thefreshstuffs.at) is currently offering stolen credit cards information for sale online where visitors can freely register and grab an account and proceed with the actual purchase. The E-shop is currently the tip of the iceberg in terms of the OSINT data and information including threat intelligence research that we intend to share in a series of upcoming blog posts and white papers including case studies on how to properly use Maltego in combination with WhoisXML API so as to give your OSINT research and analysis activities the proper boost by using and utilizing one of the Web’s and the industry’s most in-depth and comprehensive domain, IP, and real-time and historical WHOIS records databases.

Sample Web Site Screenshot of the Stolen Credit Card Selling E-Shop Hosted on the Bulletproof Hosting Provider Infrastructure
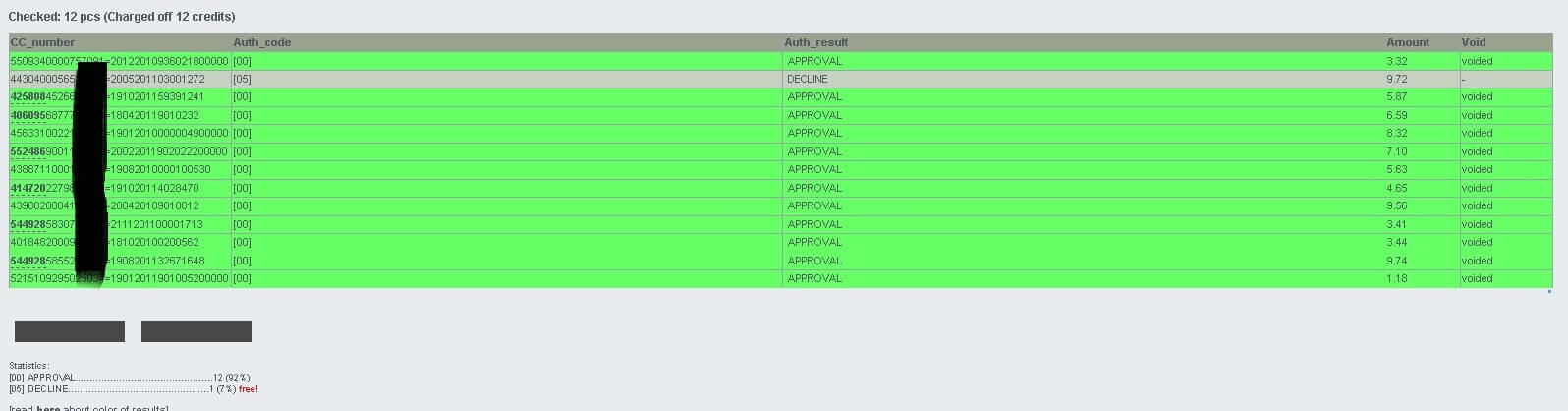
Sample Web Site Screenshot of the Stolen Credit Card Selling E-Shop Hosted on the Bulletproof Hosting Provider Infrastructure

Sample Web Site Screenshot of the Stolen Credit Card Selling E-Shop Hosted on the Bulletproof Hosting Provider Infrastructure
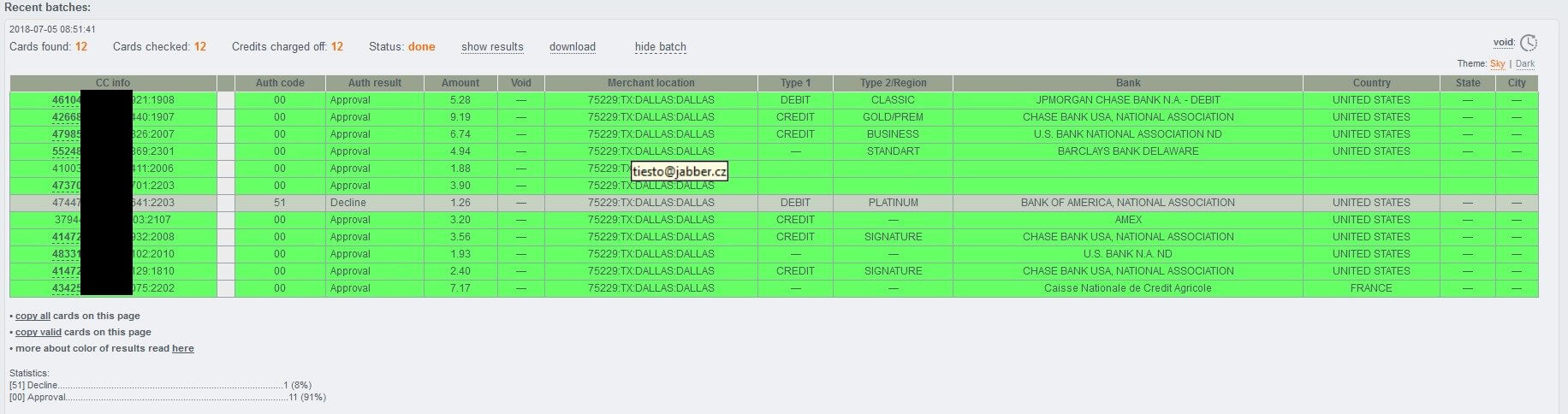
Sample Web Site Screenshot of the Stolen Credit Card Selling E-Shop Hosted on the Bulletproof Hosting Provider Infrastructure
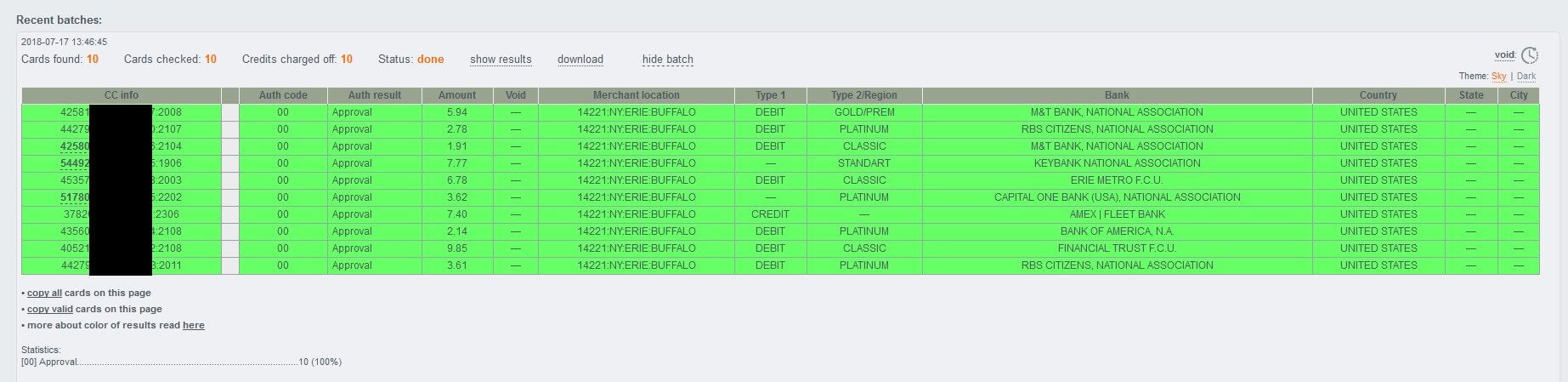
Sample Web Site Screenshot of the Stolen Credit Card Selling E-Shop Hosted on the Bulletproof Hosting Provider Infrastructure
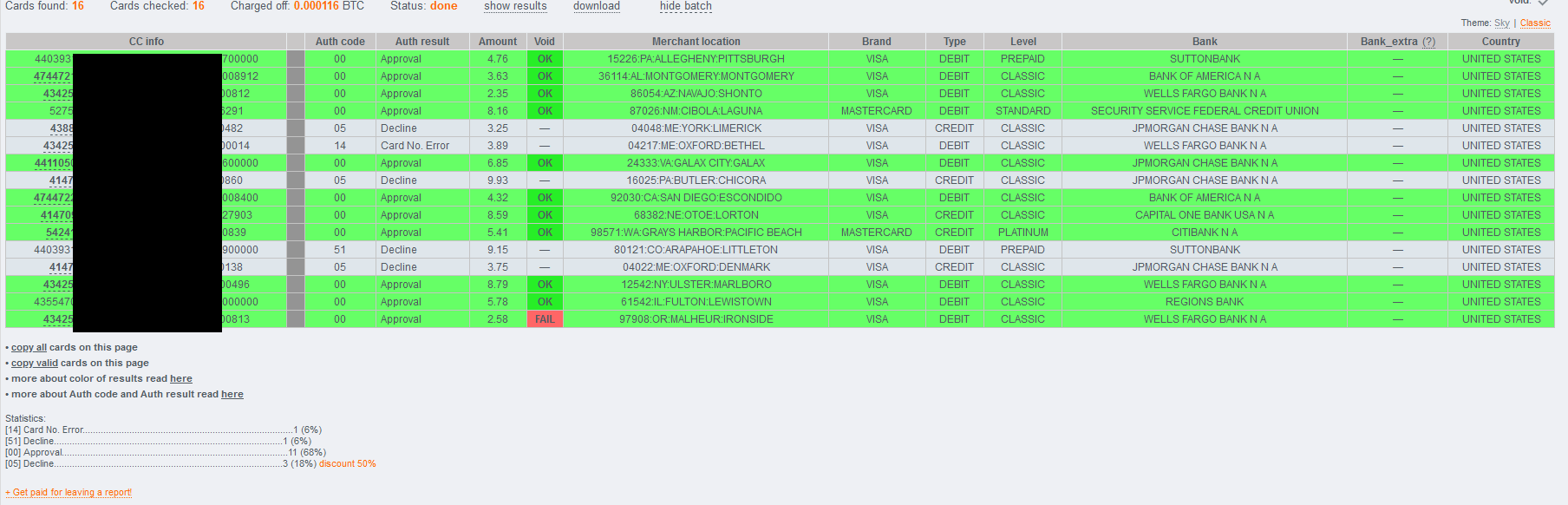
Sample Web Site Screenshot of the Stolen Credit Card Selling E-Shop Hosted on the Bulletproof Hosting Provider Infrastructure
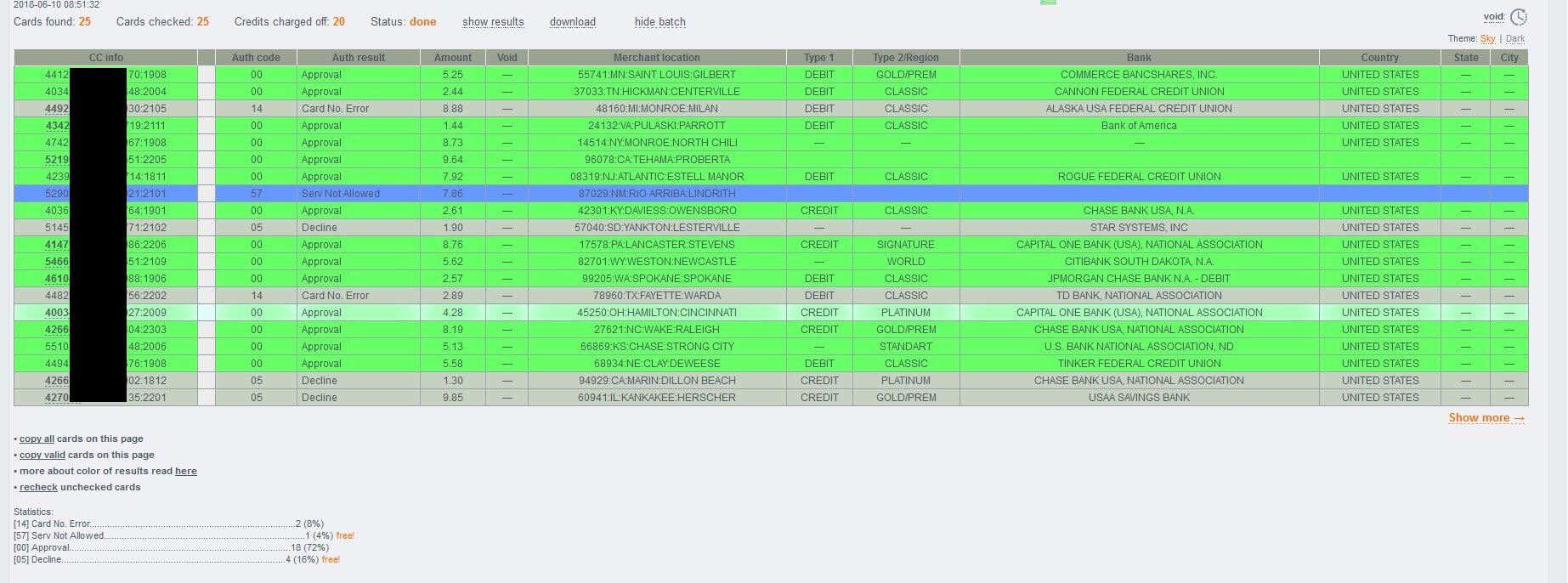
Sample Web Site Screenshot of the Stolen Credit Card Selling E-Shop Hosted on the Bulletproof Hosting Provider Infrastructure
Sample name servers used by the fraudulent and malicious E-shop for stolen credit cards information:
- ns1.hostingerza.net 37.34.176.37 ? 10800
- ns2.hostingerza.net 37.34.176.37 ? 10800
- ns3.hostingerza.net 197.44.54.172 ? 10800
- ns4.hostingerza.net 186.74.208.84 ? 10800
Conclusion
We expect to continue observing a rise in bulletproof hosting infrastructure providers including an increase in high-profile and cybercrime ecosystem relevant clients and underground market participants. We also intend to continue profiling and exposing them largely relying on the use of Maltego in combination with WhoisXML API’s integration which is basically one of the Web’s and the industry’s most in-depth and comprehensive domain and IP including real-time and historical WHOIS databases.
Read other articles


































