How to use WhoisXML API in Combination with Maltego for Advanced Mapping and Reconnaissance of Botnet Command and Control Infrastructure Using Hostinger’s Legitimate Infrastructure
Table of contents
- Executive Summary
- Introduction to WHOIS XML API
- How to get a proper account
- How to install Maltego
- How to use the WHOIS XML API Maltego Integration
- Profiling a Botnet Command and Control Infrastructure Using Hostinger’s Legitimate Infrastructure - A Case Study
- Basic OSINT Enrichment Process
- Conclusion
Executive Summary
With more cybercriminals popping up online for the purpose of causing havoc and widespread damage, it shouldn’t be surprising that both legitimate and purely malicious infrastructure is active and vigorously abused so as to host malicious software spam and phishing emails. That includes infrastructure used as a botnet and malicious software C&C (Command and Control) channel, potentially undermining modern IP and domain reputation techniques and current and ongoing threat intelligence efforts potentially serving the needs of the bad guys who often rely on legitimate hosting provider’s infrastructure for their malicious and fraudulent needs, which also includes the actual hosting of malicious software and the actual C&C (Command and Control) hosting infrastructure.
We’ve recently detected and profiled a currently active botnet C&C infrastructure that’s exclusively using Hostinger’s legitimate infrastructure for actual C&C communication channel and decided to provide in-depth analysis and report on the topic to further emphasize how the bad guys are actually using legitimate infrastructure for botnet C&C communication channel with the idea to provide timely and relevant as well as actionable threat intelligence on the infrastructure.
The campaign relies on Hostinger’s legitimate infrastructure for botnet C&C communication where we’ve also managed to identify the actual domains and IPs in questions including the actual MD5s that are currently in circulation and we’ve decided to share the results of our findings in an in-depth and comprehensive report on the topic.
Introduction to WHOIS XML API
WhoisXML API is one of the Web’s and the security industry’s primary destinations for threat intelligence and cybercrime research, including OSINT types of domain, IP, and current and historical WHOIS data records with billions of domain, IP, and WHOIS records within WhoisXML API’s database. Novice and experienced cybercrime researchers and threat intelligence analysts, including OSINT experts and analysts, should consider adopting WhoisXML API’s products in their arsenal of OSINT tools and public database repositories and databases, largely considering the tools offered as their primary information sources and threat intelligence gathering solutions and publicly accessible databases for use in their current and ongoing OSINT and cybercrime analyses including threat intelligence type of investigations.
How to get a proper account
Cybercrime researchers and threat intelligence analysts interested in obtaining access to one of the Web’s and the industry’s most comprehensive and in-depth data set of real-time and historical domain IP and WHOIS information should grab an account from the following URL - https://main.whoisxmlapi.com/signup in order to begin their OSINT and cybercrime research including their threat hunting and threat intelligence gathering process.
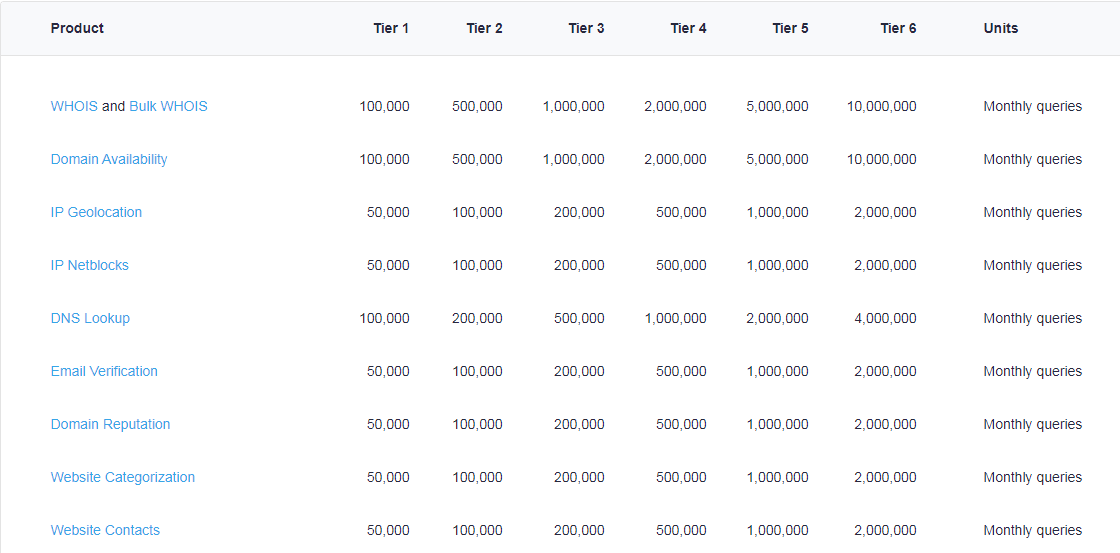
Sample WhoisXML API Pricing Plans Web Site
How to install Maltego
For the purpose of this case study we’ll use the popular OSINT gathering and enrichment tool Maltego, which you can grab from the following URL - https://www.maltego.com/downloads/ to begin using and utilizing WhoisXML API’s advanced domain, IP, and historical and current WHOIS information and one of the Web’s and the industry’s most comprehensive and in-depth databases.
Sample Maltego Download Web Site
How to use the WHOIS XML API Maltego Integration
Before using Maltego users should follow the instructions and grab a proper WhoisXML API account which they can later on use for the actual research and OSINT research and analysis, including the actual enrichment process.
Sample Maltego GUI Interface relying on WHOIS XML API’s for OSINT research and analysis and actual network and domain reconnaissance and footprint including actual enrichment
Users should then proceed with the actual OSINT research and enrichment process by importing the domains and actual IPs for their research in questions directly into Maltego by using the import feature or by manually adding them in order to actually begin the actual OSINT enrichment and research process.
Profiling a Botnet Command and Control Infrastructure Using Hostinger’s Legitimate Infrastructure - A Case Study
In this analysis and research, we decided to share and profile the activities of a currently active botnet C&C communication network which is exclusively using Hostinger’s legitimate infrastructure for C&C communication, potentially undermining modern IP and domain reputation efforts and serving the needs of the bad guys who are currently busy launching malicious campaigns and using Hostinger’s infrastructure as a C&C communication channel.
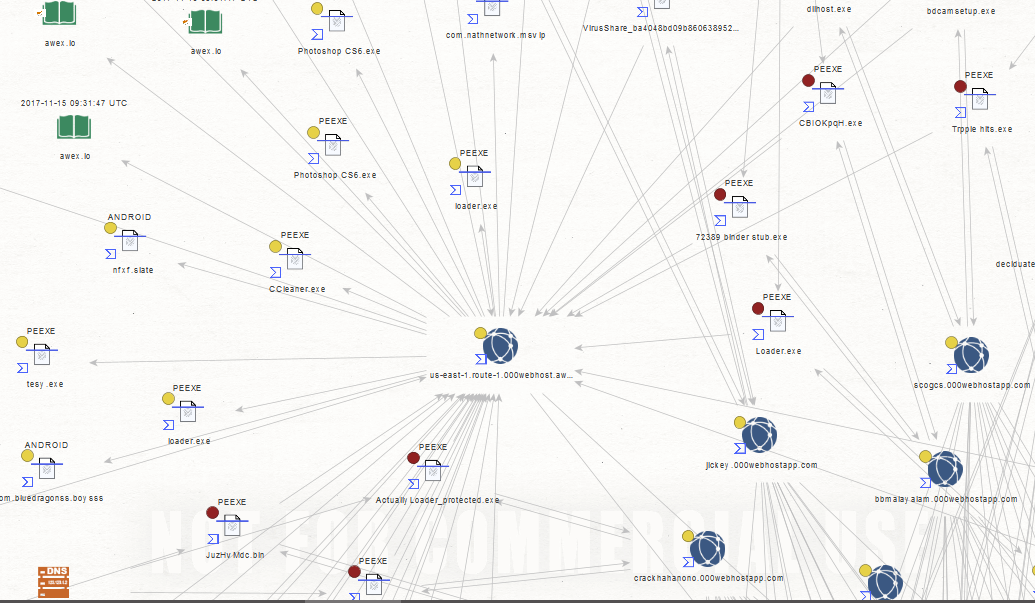
Sample Maltego Graph Analysis of a currently active Botnet C&C infrastructure using Hostinger’s legitimate infrastructure
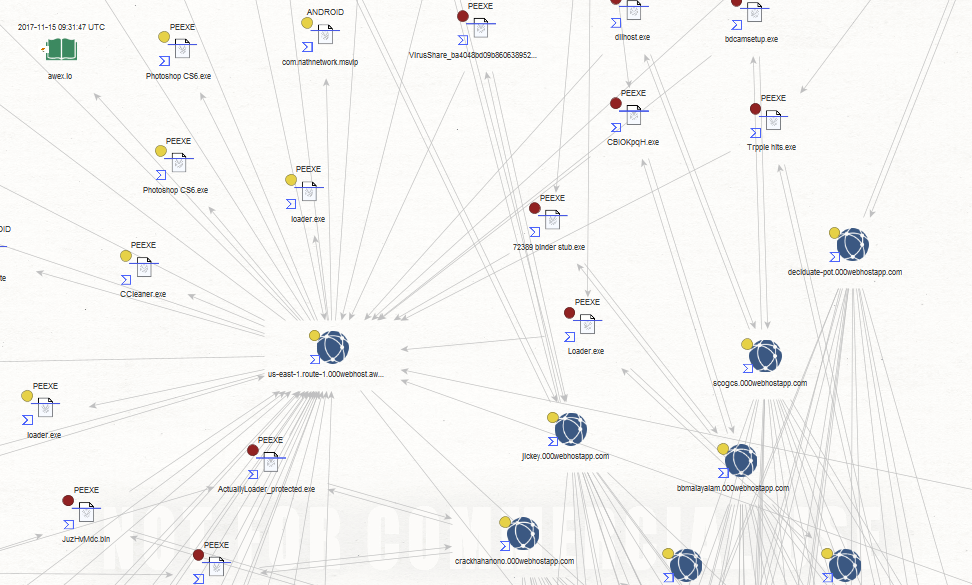
Sample Maltego Graph Analysis of a currently active Botnet C&C infrastructure using Hostinger’s legitimate infrastructure
Basic OSINT Enrichment Process
In this analysis, we’ve decided to share the actual findings based on our research which include the actual malicious IPs and the actual C&C communication channel domains including the actual MD5s known to have participated in the campaign with the idea to assist legitimate cybercrime researchers and OSINT analysts on their way to properly profile and participate in additional OSINT enrichment and processing efforts.
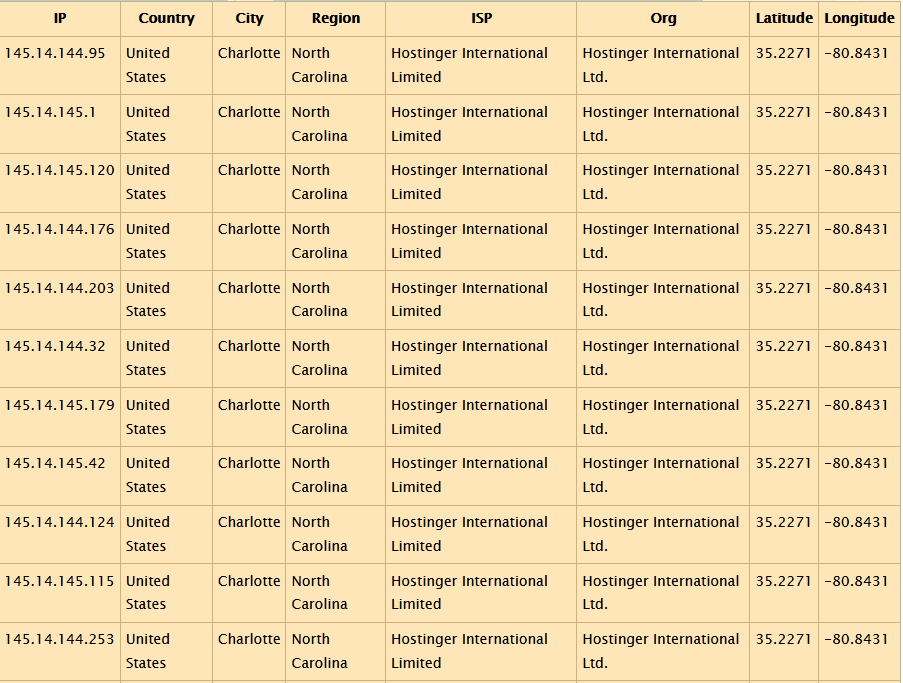
Sample Hostinger’s IPs known to have participated in the campaign and to be currently participating in a rogue Botnet C&C hosting infrastructure:
- 145.14.144[.]95
- 145.14.145[.]1
- 145.14.145[.]120
- 145.14.144[.]176
- 145.14.144[.]203
- 145.14.144[.]32
- 145.14.145[.]179
- 145.14.145[.]42
- 145.14.144[.]124
- 145.14.145[.]115
- 145.14.144[.]253
- 145.14.144[.]201
- 145.14.145[.]35
- 145.14.144[.]102
- 145.14.145[.]219
- 145.14.144[.]130
- 145.14.145[.]24
- 145.14.144[.]49
- 145.14.144[.]129
- 145.14.144[.]90
- 145.14.145[.]158
- 145.14.144[.]39
- 145.14.145[.]222
- 145.14.144[.]156
- 145.14.144[.]95
- 145.14.145[.]38
- 145.14.144[.]24
- 145.14.145[.]231
- 145.14.145[.]74
- 145.14.145[.]74
- 145.14.144[.]91
- 145.14.145[.]33
- 145.14.145[.]62
- 145.14.144[.]122
- 145.14.144[.]69
- 145.14.144[.]69
- 145.14.145[.]40
- 145.14.145[.]64
- 145.14.145[.]190
- 145.14.144[.]230
- 145.14.145[.]94
- 145.14.144[.]24
- 145.14.144[.]2
- 145.14.144[.]154
- 145.14.145[.]89
- 145.14.144[.]184
- 145.14.144[.]179
- 145.14.144[.]219
- 145.14.145[.]67
- 145.14.144[.]235
- 145.14.145[.]70
- 145.14.144[.]7
- 145.14.145[.]134
- 145.14.145[.]134
- 145.14.144[.]210
- 145.14.145[.]38
- 145.14.144[.]12
- 145.14.145[.]107
- 145.14.145[.]233
- 145.14.144[.]69
- 145.14.144[.]69
- 145.14.144[.]156
- 145.14.144[.]69
- 145.14.144[.]116
- 145.14.144[.]19
- 145.14.144[.]243
- 145.14.145[.]215
- 145.14.145[.]245
- 145.14.145[.]36
- 145.14.144[.]124
- 145.14.145[.]152
- 145.14.145[.]112
- 145.14.144[.]88
- 145.14.145[.]228
- 145.14.145[.]200
- 145.14.144[.]97
- 145.14.145[.]158
- 145.14.144[.]140
- 145.14.145[.]208
- 145.14.145[.]94
- 145.14.145[.]213
- 145.14.144[.]102
- 145.14.145[.]210
- 145.14.145[.]64
- 145.14.144[.]29
- 145.14.144[.]129
- 145.14.144[.]114
- 145.14.144[.]124
- 145.14.144[.]102
- 145.14.144[.]115
- 145.14.144[.]230
- 145.14.144[.]230
- 145.14.144[.]231
- 145.14.145[.]152
- 145.14.145[.]200
- 145.14.144[.]8
- 145.14.144[.]240
- 145.14.145[.]187
- 145.14.144[.]21
- 145.14.145[.]168
- 145.14.144[.]197
- 145.14.145[.]143
- 145.14.145[.]86
- 145.14.145[.]31
- 145.14.144[.]245
- 145.14.145[.]66
- 145.14.144[.]89
- 145.14.145[.]65
- 145.14.144[.]18
- 145.14.144[.]50
- 145.14.145[.]36
- 145.14.145[.]36
- 145.14.144[.]2
- 145.14.145[.]232
- 145.14.144[.]200
- 145.14.144[.]139
- 145.14.144[.]75
- 145.14.145[.]143
- 145.14.145[.]6
Sample Hostinger’s Free Service Domains Known to have participated in the Botnet C&C hosting infrastructure:
- azorult55.000webhostapp[.]com
- furrer.000webhostapp[.]com
- luminuis.000webhostapp[.]com
- luminatebase.000webhostapp[.]com
- doohs11111.000webhostapp[.]com
- name242215315.000webhostapp[.]com
- sakall.000webhostapp[.]com
- perdej.000webhostapp[.]com
- hooktronic1.000webhostapp[.]com
- updnaral.000webhostapp[.]com
- naralupd.000webhostapp[.]com
- gogfree1.000webhostapp[.]com
- theblackfun.000webhostapp[.]com
- hyker.000webhostapp[.]com
- rulletedonut.000webhostapp[.]com
- benzemahaha.000webhostapp[.]com
- karamlol.000webhostapp[.]com
- samperbbcash.000webhostapp[.]com
- karamelka1.000webhostapp[.]com
- hvhlegendpro.000webhostapp[.]com
- deathsun1337.000webhostapp[.]com
- hvhboss.000webhostapp[.]com
- elien123.000webhostapp[.]com
- danladen4.000webhostapp[.]com
- nazarvitalik.000webhostapp[.]com
- dyslexic-picture.000webhostapp[.]com
- pickel666.000webhostapp[.]com
- hvhcsgo.000webhostapp[.]com
- by1337.000webhostapp[.]com
- qukz.000webhostapp[.]com
- wannabyby.000webhostapp[.]com
- scogcs.000webhostapp[.]com
- tragee.000webhostapp[.]com
- online3130.000webhostapp[.]com
- gravyshops.000webhostapp[.]com
- romasshved41.000webhostapp[.]com
- jehard.000webhostapp[.]com
- crackhahanono.000webhostapp[.]com
- topsaller31213.000webhostapp[.]com
- fakesitexbait.000webhostapp[.]com
- doohs1111.000webhostapp[.]com
- get-free-btc.000webhostapp[.]com
- batka228.000webhostapp[.]com
- gtxlpfirefly.000webhostapp[.]com
- tokorankoscr.000webhostapp[.]com
- gravyshop228.000webhostapp[.]com
- spede.000webhostapp[.]com
- gamesenser.000webhostapp[.]com
- babkastilak.000webhostapp[.]com
- opera3773.000webhostapp[.]com
- deviceful-errors.000webhostapp[.]com
- jddjj4j4j.000webhostapp[.]com
- gravyshop111.000webhostapp[.]com
- sashavpisdu.000webhostapp[.]com
- whyuneedcrackfakesitehaha.000webhostapp[.]com
- vzlomvimeworldv3.000webhostapp[.]com
- doohs.000webhostapp[.]com
- grabberweter.000webhostapp[.]com
- m11necraft.000webhostapp[.]com
- jiemoh13.000webhostapp[.]com
- st11llers.000webhostapp[.]com
- superoleggamer.000webhostapp[.]com
- stalkershops111.000webhostapp[.]com
- 8989898989.000webhostapp[.]com
- gyjn.000webhostapp[.]com
- pizdaruly.000webhostapp[.]com
- planktondavid.000webhostapp[.]com
- sosatsuki.000webhostapp[.]com
- basest-rooms.000webhostapp[.]com
- starf1.000webhostapp[.]com
- ha4cker.000webhostapp[.]com
- tribunitial-impulse.000webhostapp[.]com
- pizzamazz.000webhostapp[.]com
- baxinyo.000webhostapp[.]com
- wedro228.000webhostapp[.]com
- jayrolzcashout.000webhostapp[.]com
- josephgrief228.000webhostapp[.]com
- homiletic-submarine.000webhostapp[.]com
- sharjoff.000webhostapp[.]com
- stalker098.000webhostapp[.]com
- jlckey.000webhostapp[.]com
- narkoman1337.000webhostapp[.]com
- bbmalayalam.000webhostapp[.]com
- paufx.000webhostapp[.]com
- nvutionefasfsa.000webhostapp[.]com
- gamervordl.000webhostapp[.]com
- swandersd.000webhostapp[.]com
- davidosik228.000webhostapp[.]com
- sber-host.000webhostapp[.]com
- patrilinear-mixture.000webhostapp[.]com
- deciduate-pot.000webhostapp[.]com
- ziggeroff.000webhostapp[.]com
- geggegegegegeg.000webhostapp[.]com
- appeq.000webhostapp[.]com
- lasinka.000webhostapp[.]com
- roling.000webhostapp[.]com
- absorbent-spokes.000webhostapp[.]com
- polarisp0laris.000webhostapp[.]com
- pate1k.000webhostapp[.]com
- fesfesfsefes.000webhostapp[.]com
- azorult2410.000webhostapp[.]com
- discaredforftp.000webhostapp[.]com
- opira.000webhostapp[.]com
- yaroslavdimitriev.000webhostapp[.]com
- pssa.000webhostapp[.]com
- funpay1.000webhostapp[.]com
- josephgrief.000webhostapp[.]com
- weilbrain01.000webhostapp[.]com
- logiakk1i.000webhostapp[.]com
- nikitaakimenkoklass.000webhostapp[.]com
- stalkeronline1.000webhostapp[.]com
- uraganhokino222.000webhostapp[.]com
- patayka.000webhostapp[.]com
- mixaton.000webhostapp[.]com
- xinchaocacchau.000webhostapp[.]com
- filess2.000webhostapp[.]com
- ww6.000webhostapp[.]com
- auxinity.000webhostapp[.]com
- sinkable-ingredient.000webhostapp[.]com
Sample MD5s known to have participated in the campaign and to be currently communicating with Hostinger’s Legitimate Infrastructure for botnet C&C purposes:
88849b8f6a9c9760df5aaa825c3b31a1a10bddb8698318e02c5f5b180fdeeb9f ebf3dc1aa5c27baa10c6c85c0d9e82d00f20ff24153fe74812fdbed68f55d20e 43ad2ae619637a367659348969612a77f49e7e57e23ab1455a9240728af94ef8 13e451081374d403dc828c5b156aaebbd987f52b937c0964bdbd84c4aff9c1a2 f2efa2ecf699b83e2ca0bdbf52149d31cdf729a41b2d59e017f20acb21956784 9d0a5ec50621224534f3e2320172b20c3aebae320aa6de39b33fd07f649ee5e9 63c8752865f254e26f15d86ddb967d7c43270910a98fea33179741f2a7598dc8 be9d16570ebc968cf4e04349610c9ab4ac6eba6e334452f7a9697cb61b83bf58 1045241f26746ac094c5661e1c85e9a34157bbb8bd412537fc3f310b6d97dda9 8c359793b141f8ee152000532d1eb8141cce06dc947f430d7bfefec975ce5821 288ef12ede066b889f87d69aef23467192712613a5f9ff7cd64d2ad7abd46bd8 a7a1f42353d5e0b8beecef99aeb08f9c0c93c2ca9985ff26a24a1e3341082a79 4ae5e427577b2b915169b1ce7203614b8ee0443993ca5ccbefd50c9eedfc870d d7fce214fa966de20b14f8867a25cf29f87146cc46399be14c398d0cce2f6451 3ab526ed35e1423b7edfec603010164850fbf60df62752f5a30ca9409af5d6a0 271973ff6a3278c4a12ac265c2abbf369f67bb5c39f3574fe68dbc7f922e1812 9ad06ae676239a1d0a30f1b22fdeb2c12c88836b9acd7e0316477e914fe9cdb5 ef1e8a81a75b40320a0cefaaf1e4978989b2b0f9c21c80a24e6fba100e303c71 82fbbec39e5294475094c4235da66da314b954a15d633daaed2a05e3f8dc4531 c1a6387b011461afeca78e254875b5dcae22a3eff6f82cfaf62f71695abe3ba1 26ae23e34739fa9747b1ebca742c7faad407b328afe9ee495e31531ef74aafdf c1f8ab7a29428c7670c9a8a36c23cf55fbcfa3baa3c0ca458c72c13a59bae299 b978ed7c6e16b7d379575467ea938f89f3f32ec0c42e59593494f73341dc81fe 9c777d5e8988bce8a73452def7ca806eaed32eb05b372e906cc0922fb0ca95ed afb227feb86b65c2b01cb68847259d85b9710980ed34dc332b9a4948a99d0b68 acc2d8846d6b6bdc4face6843522d1279c791c73a7b8637f4cf25afe35d469bd 7328970f882660f95abaca4e44b58c3dc0e0a22d7984795791477617570743b7 4dd46cc1711ec4dbc2038bff8be505baaa08322ffded20f7decaa60eb55191f2 a46ea9d06a390cb1ed765d22e12f5dfa58ea68a967824946751cd46eae441e0f 98cc3044493f2876ecc774b209b31869d175694f1daa6b2c5383114a0382eb83 0b97905330043bb4064006897f0db31812add817ee0fb69596953ea525cd6460 0b2b05216a4449c6204c84a2b0cf43c3a8188b53e29be1f83b858bd1b7f8c417 9a87209923f4cfe81fee5bbf13e8dfcab78732258b0e8a87d2a43d202d33a062 46639679ec57bb38dfba3cb459dee26da862d5515e6e17da9c0c4c87c073f2de 8741527fd2974bdc86c087175b07201cce897518dc07d7dbfa212ff5dedb8c33 2de83614000e84f0891dd7955f1e346f3992ccac9e3d01d7bc64b58df3e45003 aebf4efec271b2a97656c8c413d50e3336a2aa8fd4d3ef4610d5ba4406919fe1 a0a7dec94394bb3dfa0a4660c2ce8523b0a01e004a9a8ddcf0ff352cc2854960 bd31a197cb8765b5c510807e63edb60956d9c0ea91228b221ff4d7e6ea79495d e2f3b4feef0f02ce46e2d68015f146fe9924c92611abf486d32fa140c1d2ce7c 493438299ec5967c39e341242ead849bc202216bd582a589836108d5bf4c1fda b73019268d92907ce1ec54cdbe2c67fdf4d0418360bf5dfcbce64ec3a9777751 15f3b8d5948dca9532a8578147935f812d684cbcfb3cc6ad2bd861f048c2b5f1 dd448148bec5fcee7d6dec71b10b320704b96b0eddc4c0b3f8294dc351c0d726 3a317c7fe889e73059589136334a063a5cab57f57bf6d31192455f74d16f3b46 a3d4071f5c2aded895cf29a4efcfa3fa134d1b992b5b884ab9010f9af4d56030 604dc7e88c8de2aa8c9e3b7917be25b42fe41b9702fd1a2f35b1c09372d5bd35 5ca3f43e97cfbcb135804e430fc88f7d26287d924514b34b8ec11159e1c36fcf dd860b1b9612e733d8f0985148b1f47cd9361243ccb729c3b6c3c2280461e157 9896b67d6f15543de5b6fb876688fc3a4d1c77ad7ed822c8a67e2572dccad5f3 ec693ab83d9b4f8cbf2d3321124ad11aad3f24ea62d58bcb53965d8cafb07ecf f6a9251a6c5ef576e4a6a50257e971dc3096c2e6e9605b815e562e0350be9c2e 4dd771413bedcc55cd73cc8f3c75ffdd4b00cc84853bce2b62fc48dc178a087e ff6e3f1adb64bd83cb7c39e6f6a8d9710bc661cab92a5b2a8f605d36c84e17ae 8fa9eb00743b99f094b6349a27deb6f617094c01f0410361ef7eee041f8de66a 98d9a977a51bf3d678665c324ff367898cdd2aeeb76fb561f20568144325e6e7 643f6a92da2744df02d9a918c30736c9c95c2428b8b5c0829229e92eade4fc5d 170c7ca8940d943aba7733850dc821666faeee288bcfd9f4888679eca5eee8a3 9e804f7c1a2af557a676b0a6c2f16896795db09b374a8de72ea6e9b05956f77f 3f2fff9109a955147c2f8c004eaf149e02b877e0773d3548e6715f6d1ee89518 3e08d15b089e8204f02f74a1c37705f7e741fafd2ca39a637499976ce401b89a a5883aea6aab88764a92e1c55b536c9689a57a5f643533724429b4d7dbe883b2 ad3dd8f71b11cc3b56b7282580359d06b21e40a6f851c78957e0e9d084f4d6e0 8e9dff519eec6d5aee5f4f02a45b7210895038a089a3dcb2de0486ac32a8f585 ff4fd920ef06006441571ac2cf9f8234ed16707e4b5505d66c343fadbcb244f6 298b3752e285ca528d21b9a4bcaced61a88cd61ec7e9fe7a9cd8219c9fdb2ede 2aef15daa41518f80423a5ddee02f67a7598876510e927bbe56ad3f01ff22840 06922c21424fd65bfa11e3478911450735e3fdae6e11f28ed3e5af635b9cb789 9b36becb449b8d0c5cd81644f07df1d75a66bb6fceb1982825cad985c47ba222 b700e835817b1561fb7bb5159f2e61867305caf15a75e5dff84cbaa6fe20f8be d91b20cdc2e25badf34d528426b7c9b7993974b417935e0272c48d310011fb1c 474005c50d35b50556f7b7a8deace4dbec86cec0a5741a72c510aa34ec5af532 6030b160dc7ae7d603ad792b59b8f2d4b3eaefd915130a3231d120d1052e4457 c515792b03d478cd3e62ab656f282c58602d945839f74c633d024703d4c17bd2 9420aff489e9ad332b87b2a2b660fe88d82a0fca732ee10fac213387d066de03 e59d3b262a84746e2f59f202e83413705e54c58c5e54f915c7c19e8866f8d6bc b641ee5295294f1b7b1385b4eb625b255930c8b6dbf80f65f5d279f7b78322db 8b94413c149f5ab2f8b5bf7bd523ce0136907850e12846a55b6159d29b7c9fe7 aa1e95fd2ca3373d46b0beb562553acd32cdfa16addd73bcc2e3df7439aed503 e865410e38a2cd2fbcaf9d51db1686c0d2b315337d01696ff03a4e103460930e 047915ca9ecfcd899c48d06c7ab217c1d6fbca935b266d62bcd46a6fb3f11ce3
Conclusion
We expect to continue observing an increase in legitimate infrastructure abuse courtesy of the bad guys and we’ll continue monitoring these campaigns and publishing our findings in a series of white papers and reports, including relevant case studies.
Read other articles


































