The Most Common Types of DNS Attacks Explained
The Domain Name System (DNS) is one of the most crucial systems that make the Internet work. It is commonly referred to as the Internet’s phonebook, though it may also be compared to a Global Positioning System (GPS) that points domain names to the correct IP addresses.
The DNS is intricately involved in almost every Internet service—websites, chat services, email services, and social media sites. Subsequently, it is a common target of cyber attackers. One of the most famous DNS attacks occurred in October 2016, disrupting the services of several high-profile websites for about 18 hours, and some of the affected websites were PayPal, Twitter, Netflix, Amazon, and Spotify.
DNS attacks are menacing and could affect millions of people. Also, they are among the most prevalent forms of cyberattack. In fact, about 83% of service providers experienced a DNS attack in 2020.
The most common goals when performing any type of DNS attacks are:
- Stealing user credentials
- Injecting malware into users’ devices
- Obtaining sensitive website data
- Defacing an organization’s website
- Installing ransomware
This post looks into some of the most common types of DNS attacks. We also provided some examples, along with tips to prevent them.
What Are the Types of DNS Attacks?
There are several types of DNS attacks, and we will explain six of them in detail here. The types of DNS attacks described in this post are:
- DNS hijacking
- Domain hijacking
- DNS spoofing
- DNS tunneling
- DNS flood attacks
- NXDomain attacks
- Phantom domain attacks
- Random subdomain attacks
- Distributed reflection denial-of-service attacks (DRDoSs)
DNS Hijacking
DNS hijacking is the process of maliciously altering DNS resolutions to redirect visitors to malicious websites. A rogue DNS server is set up by the miscreants that resolve legitimate domain names to modified, malicious IPs. A malware is then distributed to configure devices of the users to use the rogue name server instead of the normal one provided by their ISP or organization. This is also referred to as a DNS or user redirection attack. With DNS hijacking, threat actors typically infect the DNS with malware that runs automated scripts to change DNS configurations.
When users type a domain name into their browsers, attackers send a fake IP address allowing the browsers to display a different website. This bogus website often looks like a legitimate site to make the victims believe they are on the right webpage. The perpetrators would then be able to steal any data the users input into the fake site.
Examples of DNS Hijacking
In 2013, users who wanted to visit The New York Times and Huffington Post websites, among others, were redirected to a malicious server. This happened after the Syrian Electronic Army (SEA), a cybercriminal group, gained control of the websites’ domain registrar’s system through a phishing email.
DNS hijacking attacks also made headlines in 2019 when threat actors attacked more than 40 companies, allowing them to steal sensitive data, including user login credentials. The attack was believed to have been state-sponsored, and the threat actors could have gained access through phishing emails.
How to Prevent DNS Hijacking
The first step toward preventing DNS hijacking is to deter the entry of malware into an organization’s network. This can be done by educating network users about phishing emails and constantly scanning for and blocking suspicious traffic. A zero-trust approach would also be beneficial not only to the organization but also to its website visitors and service users.
Domain Hijacking
Domain hijacking differs from DNS hijacking, as it involves altering a domain name’s registration records. Still, the goal is typically the same—to redirect users to a malicious server that attackers manage.
Domain hijacking can be done by gaining unauthorized access to a domain name registrar’s system. In some instances, threat actors impersonate the domain name owner after obtaining his or her personal data through illicit ways. They would then ask the registrar to change the domain’s registration records.
Once attackers gain control of the domain name, they can redirect visitors to their servers that host spam content or malware.
Examples of Domain Hijacking
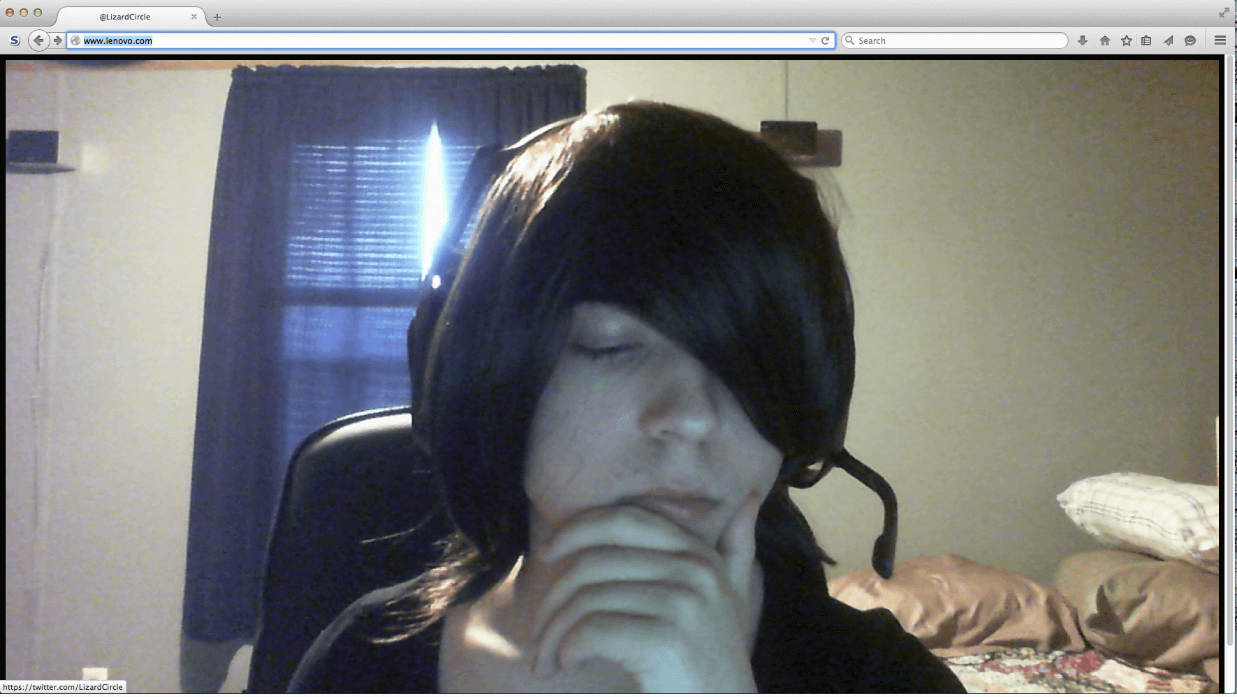
One of the most famous cases of domain hijacking involved lenovo[.]com back in 2015. Users who wanted to visit the website were redirected to a page that displayed a picture of someone sitting in a bedroom.
The same thing happened to Google’s Vietnam search page. Apparently, the attacker was able to change the domain’s registration records through a Malaysian domain name registrar.
How to Prevent Domain Hijacking
While the examples of domain hijacking above only featured website defacement, worse things could happen. For instance, users can get redirected to pages that contain information-stealing malware.
To prevent domain hijacking, domain owners are advised to choose reputable domain registrars, especially those that grant DNS Security Extensions (DNSSEC). The latest security patches should also be applied to web servers as soon as these are made available.
DNS Spoofing
One of the most common types of DNS attacks is DNS spoofing, also known as DNS cache poisoning. The attack is relatively straightforward, but it is vital to understand that the domain name system is a big distributed database with many servers. Some are the authoritative ones for, for example, a domain, but many others are caching servers serving an organization or a single device. These collect the name resolution results locally in their cache to serve repeated requests quickly and decrease the load of other servers. Threat actors could overwrite the local DNS cache values, so they are redirected to a malicious server.
Instead of caching 8[.]8[.]4[.]4 for google[.]com, for example, attackers can change the users’ DNS cache and point the domain to a fraudulent IP address. As a result, the threat actors would receive legitimate traffic and respond by showing visitors the malicious website. They would then be able to steal the users’ sensitive data.
Examples of DNS Spoofing
DNS cache poisoning was discovered in 2008, so it is not new. It was the suspected method of attack against the Malaysian Airlines website in 2015, months after the disappearance of Flight 370. For seven hours during the attack, the website displayed text that said “404 - Plane Not Found | Hacked by Cyber Caliphate.”
More recently, specifically in January 2021, a security company discoveredthat millions of devices could be vulnerable to DNS cache poisoning. Attackers could exploit the security flaws in dnsmasq, the DNS caching software used by many Internet of Things (IoT) devices.
How to Prevent DNS Spoofing
DNS cache poisoning can be prevented in several ways, including the following:
- Configure DNSSEC, an extension of the original DNS protocols to ensure cryptographic authentication of DNS data, authenticated denial of existence, and data integrity on caching name servers
- Use DNS spoofing detection tools
- Flush DNS caches regularly
DNS Tunneling
DNS tunneling is a method that allows threat actors to bypass network firewalls by hiding the communication within valid DNS queries and responses. For the Internet to work, DNS communication has to be allowed deliberately, and its format is not too restrictive either. DNS encodes stolen confidential data, commands to botnets, etc. into innocent-looking DNS queries. The attackers register a domain whose authoritative name server acts as one side of this communication channel, whereas on the attacked system’s side there has to be some malware running which embodies the other side.
Examples of DNS Tunneling
DNS tunneling has been used by cybercriminals to steal sensitive information and, in some cases, money. Home Depot became a victim of a point-of-sale (PoS) malware called “FrameworkPOS.” The malware was designed to steal credit card data through DNS tunneling, and about 40 million bank cards were exposed as a result of the intrusion.
How to Prevent DNS Tunneling
The specific protection against this kind of attack includes the limitation of types of DNS communication to the really necessary data content, the use of a caching name server and the analysis of its logs regularly, and keeping an eye on DNS communication payloads.
It would also be a good idea to limit data destinations by firewalls so that even when DNS tunneling occurs, the data can only get sent to whitelisted IP addresses. A DNS protection solution would then be able to detect abnormal activities, such as DNS queries, regularly being sent outside whitelisted destinations. As in other types of DNS attacks, educating network users about phishing is among the most crucial steps in preventing DNS tunneling.
DNS Flood Attacks
While the primary purpose of DNS hijacking, domain hijacking, and DNS spoofing is to steal sensitive information or deface a victim’s website, DNS flood attacks are different.
In this type of DNS attack, threat actors drown a specific DNS server with a huge number of requests until it can no longer accommodate legitimate ones. Like other distributed DoS (DDoS) attacks, the goal is to overload a victim’s assets with a huge amount of traffic until it is rendered useless.
However, the underlying reason for overwhelming a victim’s system could be to extort money. DDoS attacks can also be a front for more extensive operations, such as data theft.
In DNS flood attacks, threat actors run a script, often from several botnets. In most instances, they would spoof the packets sent by the script to make it appear that the requests come from multiple sources.
Types of DNS Flood Attacks
DNS flood attacks can come in different forms, including NXDomain, phantom domain, and random subdomain attacks. You may find these terms used interchangeably in some cases, so it’s important to know the difference.
NXDomain Attacks
NXDomain attacks are another form of DDoS attack where the attacker overloads victims’ DNS servers with requests for invalid or nonexistent records. It’s similar to hundreds of people calling a customer service hotline all at once and asking to speak to a nonexistent agent. The calls would take so much of the department’s time and resources. Legitimate callers, meanwhile, would have to wait for a long time or won’t be accommodated at all.
In an NXDomain attack, both the DNS proxy and authoritative servers will end up handling all the queries for nonexistent records. Responses to legitimate requests will slow down or ultimately stop.
Phantom Domain Attacks
Phantom domain attacks work the same way as NXDomain attacks, but the attackers’ command would request for specific domain names instead of just any DNS record. These phantom domain names are typically set up by the threat actors as part of the attack.
These domains do not send responses, so the resources of the victim’s DNS server are spent waiting. As a result, they can no longer accommodate legitimate queries.
Random Subdomain Attacks
In this type of DNS flood attack, attackers send DNS queries for nonexistent subdomains. The root domain of these is valid, but the subdomains are randomly generated and hence invalid. Again, the victim’s DNS server spends most, if not all, of its resources looking for the invalid subdomains.
Examples of DNS Flood Attacks
DNS flood attacks are often difficult to distinguish from a legitimate surge in traffic. For example, in April 2020, researchers saw a massive increase in traffic volume across five industries, including news and travel.
That was the time when people were first ordered to stay at home due to the COVID-19 pandemic. While website owners could attribute the surge to people’s behavior while at home, researchers believed that it was most likely a DNS flood attack.
The DDoS attack against DynDNS in October 2016 is also believed to have used this type of DNS attack. A huge network of Mirai bots comprising thousands of IoT devices attacked the DNS service provider’s network, affecting popular websites like PayPal, Twitter, and Spotify.
How to Prevent DNS Flood Attacks
One way to prevent this type of DNS attack is to examine an increase in DNS queries like the researchers did in the example above. The setting up of DDoS protection solutions would also help detect and block attack traffic, while some organizations implement a limit on DNS response rates.
DRDoS Attacks
In a way, Distributed Reflection DoS (DRDoS) attacks are similar to DNS flood attacks, as their goal is to take down a victim’s network. However, DRDoS attacks target a victim’s network bandwidth by sending a huge number of fake packets until the network starts dropping packets, including legitimate ones. This is carried out as follows: A network of bots sends DNS queries to a number of name servers, pretending that they were coming from the victim, thereby “reflecting” all the replies to the targeted server or network. The latter will thus encounter a tremendous amount of DNS replies which it will not be able to handle.
Examples of DRDoS Attacks
Google experienced a 2.5Tbps-strong DRDoS attack in September 2017 when an attacker spoofed 167 million packets per second (Mpps) and sent it to 180,000 exposed servers. The large volume of responses was reflected to Google servers.
The company says that it is the highest-bandwidth attack reported, four times larger than the Mirai botnet attack in 2016.
How to Prevent DRDoS Attacks
To prevent this type of DNS attack, it helps to implement advanced intrusion prevention systems (IPSs) that have DDoS protection as well as a firewall, encryption, and load balancing.
Early detection is also key to preventing DRDoS attack (or any DDoS attack for that matter) from affecting an organization’s network. In 2018, for instance, a 1.7 Tbps-strong attack was observed, but the victim did not experience an outage because it was immediately detected.
Consequences of DNS Attacks
The examples provided under the types of DNS attacks are solid illustrations of how DNS attacks can significantly affect organizations and their stakeholders and clients. The DDoS attack on DynDNS, for instance, affected millions of Internet users who were not able to use the services of the company’s clients.
While there were no reports of exposed or stolen data during the particular attack, the possible consequences of any DNS attack can be profound. After all, data exfiltration is among the primary goals of attackers. The DNS tunneling attack on Home Depot, which also targeted United Parcel Service (UPS) and Target, allowed threat actors to amass millions of credit card and bank account records.
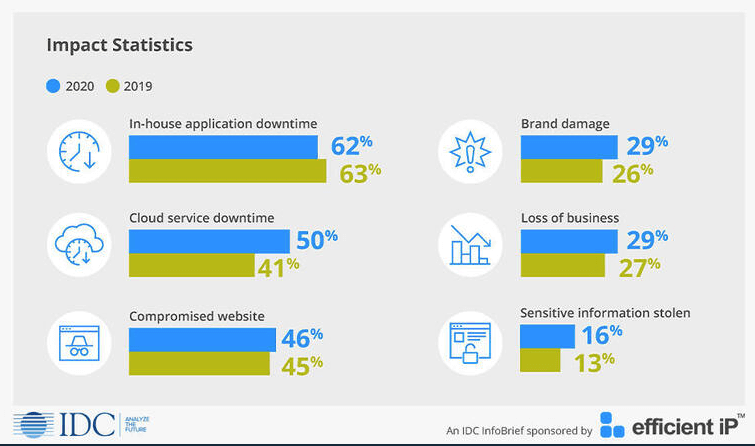
The International Data Corporation (IDC) itemized the most common effects of DNS attacks, along with their shares, in the 2020 Global DNS Threat Report. In-house application downtime took the lead with 62%, followed by cloud service downtime (50%) and compromised website (46%). Some 29% of DNS attack victims also suffer from loss of business.
Aside from these apparent effects of DNS attacks, victims also suffer from consequences that could be difficult to quantify, such as brand damage (29%) and theft of sensitive data (16%).
Conclusion
The DNS is a critical part of the Internet infrastructure, and so it has to be protected. Monitoring DNS traffic, setting DNS response rate limits, and inspecting suspicious queries are among the ways to prevent various types of DNS attacks.
Aside from these, the human factor has to be considered as well since many DNS attacks rely on phishing and social engineering as entry points. The DNS hijacking on The New York Times and Huffington Post mentioned earlier, for example, began with a targeted phishing attack against the establishments’ domain registrar.
Setting up DNS protection systems and educating network users about the dangers of phishing should go hand in hand in the fight against different types of DNS attacks. In both areas, a zero-trust policy would be ideal.
Read other articles