Leveraging Cyber Threat Intelligence: Must-Dos for Companies To Prevent Phishing and Other Attacks

While phishing is considered one of the oldest threats in any cyber attacker’s arsenal, it still manages to work. The targeted organization or individual, social engineering bait, and the manner in which information gets stolen or malware is delivered may change. Still, the motivation often remains: to take someone’s details or even identity.
In many phishing scams, cybercriminals opt to create a fake company pretending to offer services that may be hard for users to resist. Such is the case of two confirmed phishing domains we analyze throughout this piece—technoarubacloud[.]com and teichdata[.]at. Any visitor lured to avail themselves of these two fake suppliers’ offerings is likely to be tricked into handing over personally identifiable information (PII) to the criminals behind the bogus sites.
In short, phishing and cyber attacks in general will continue to occur. So how can individuals and companies alike prevent themselves from falling into information-stealing traps? Following the four-stage process in this post aided by reliable cyber threat intelligence solutions may be the answer.
How to Use Cyber Threat Intelligence to Address Phishing and Other Attacks
Part of cyber threat intelligence efforts entails scrutinizing one’s Web properties for misconfigurations and weaknesses that cyber attackers may abuse to get what they want. It also means dissecting every domain, IP address, and email address that one comes into contact with for signs of malicious activity.
Note, though, that threat actors have many ways and means to hide their nefarious activities, making detection and consequent blocking difficult without the right techniques, resources, and tools. Overblocking may also prevent legitimate visitors from accessing websites and pages. With these considerations in mind, let us take you through a step-by-step guide to achieve better cyber threat protection.
Stage 1: Detection
The first layer of defense against any threat is effective detection. By proactively identifying harmful pages, users can easily avoid falling for traps that threat actors set. For instance, with solutions like Domain Reputation API and DNS Lookup API, they can refrain from visiting websites that may be malware hosts, redirect to malicious pages, or are known dangerous or suspected entities. Here’s how:
Detecting Phishing Domains with Domain Reputation API
Users can integrate Domain Reputation API into existing solutions to automatically check if a domain they wish to access or communicate with has ties to phishing activities. Take, for example, one of the domains cited previously—technoarubacloud[.]com.
We ran it through the API and found that, apart from having a low reputation score, it has a recently obtained certificate and is listed on PhishTank. These are clear signs that the domain may not be safe to access.
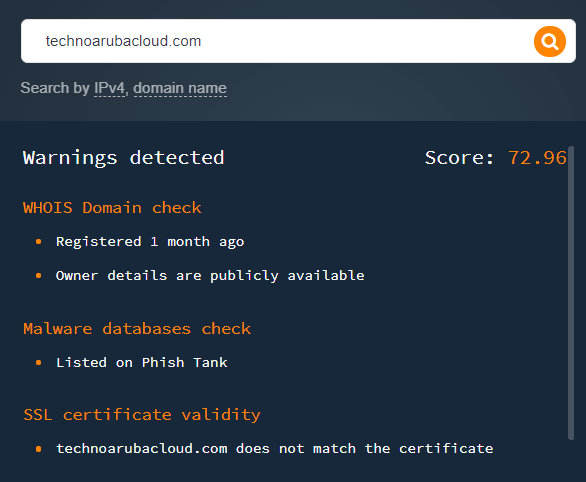
Users of Domain Reputation API can configure their systems and devices to block access to domains with low reputation scores automatically. That way, they will avoid becoming a victim of phishing attacks.
Detecting Dangerous Domains with DNS Lookup API
Users can also opt to integrate DNS Lookup API into existing solutions to monitor for updates of interest in DNS records. For example, running teichdata[.]at this time shows the following:
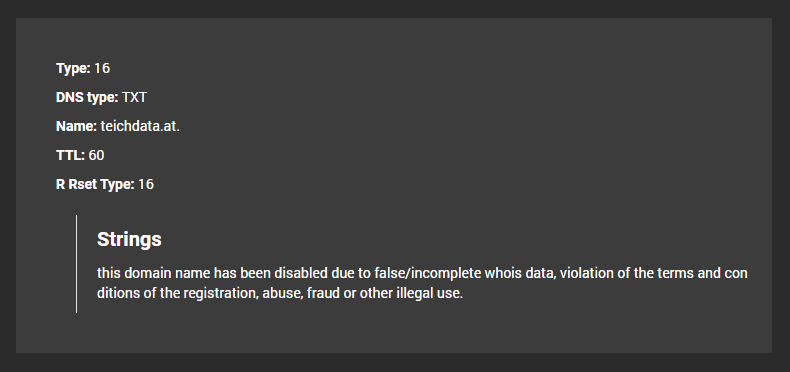
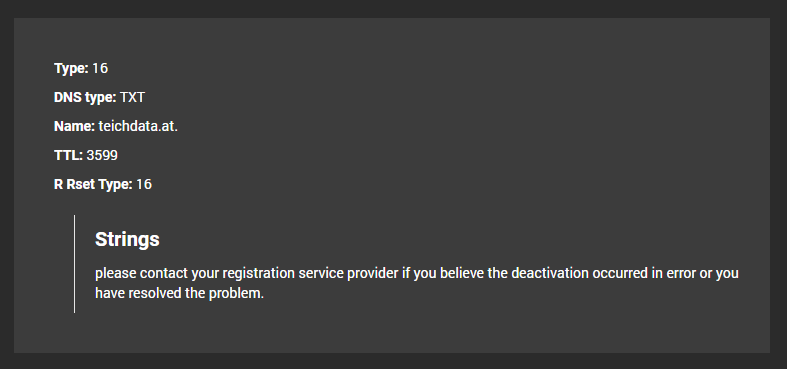
Indeed, teichdata[.]at has been “disabled due to false/incomplete whois data, violation of the terms and conditions of the registration, abuse, fraud or other illegal use” — meaning it’s currently down, probably due to foul play.
Interestingly, a few weeks before the site was deactivated, Threat Intelligence Platform (TIP) had detected the domain’s recently obtained SSL certificate:
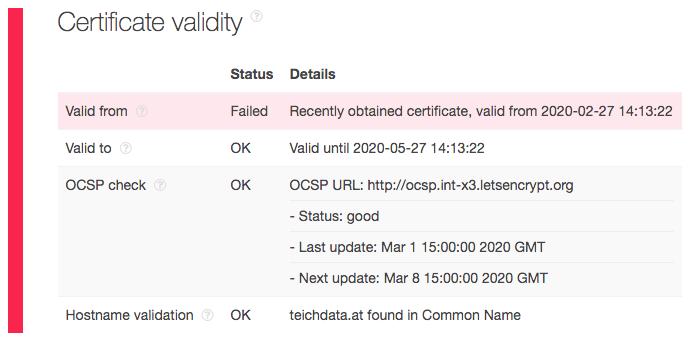
Of course, not all domains with a newly issued certificate should be considered malicious. But the above illustrates that it can be relevant to handle such sites cautiously — bringing us to the reconnaissance stage.
Stage 2: Reconnaissance
Every time an attempt on one’s organization is detected, it is good practice to dig deeper. All related domains, IP addresses, and email addresses may need to be investigated further. Several products can help, but we used two in particular for demonstration purposes.
WHOIS API/WHOIS Database Download/WHOIS Search
A WHOIS lookup will reveal the owner of any domain or IP address. For example, we queried teichdata[.]at on WHOIS API and found that, while its registrant’s details aren’t visible, we were able to get an email address (der_fan@mail[.]ru) that can help us with our investigation.
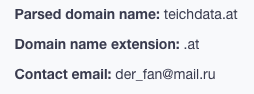
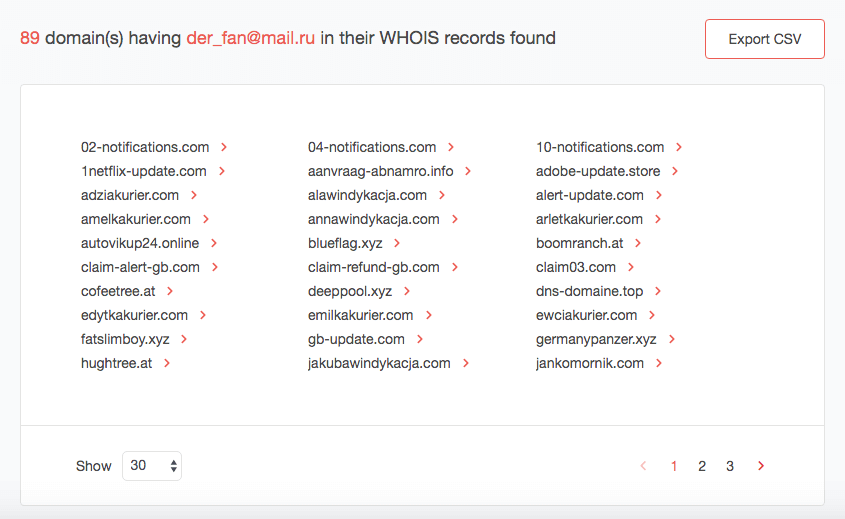
Reverse WHOIS API/Reverse WHOIS Search
Users who want to avoid all contact with the known phisher can do a reverse WHOIS lookup by using his email address as a search term. They will get a list of all domains whose records contain it. Adding the domains to one’s blacklist as a precautionary measure may be a good idea, too.
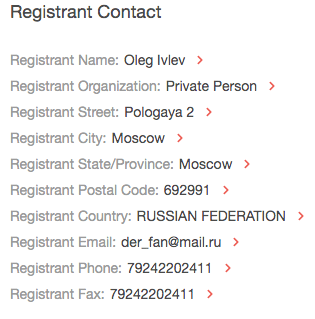
WHOIS History API/WHOIS History Search
Sometimes, users can get lucky by building a historical WHOIS report for privacy-protected domain registrants. The historical WHOIS report for adziakurier[.]com, for instance, gave us a registrant name—Oleg Ivlev.
Users can look for other domains and IP addresses containing the registrant’s name as well. That information will also come in handy in the next stages.
There are various other solutions useful for the reconnaissance stage. Apart from WHOIS and reverse WHOIS lookup tools, many cyber threat intelligence products that use a domain, an IP address, or an email address—typical IoCs given in threat news and reports—can serve as part of an investigation. These include but are not limited to the following:
This should list all details about the queried term’s corresponding domains (if any) and DNS records. It also gives a domain’s corresponding IP address.
IP Geolocation API/IP Geolocation Data Feed
This lets users know where the owner of the IP address originates.
IP Netblocks API/IP Netblocks WHOIS Database
This allows users to identify the regional Internet registry (RIR) responsible for an offending IP address within a given range. That information is useful in the third stage.
Stage 3: Takedown
While private individuals or even organizations are not allowed to take down a malicious domain, they are encouraged to report and submit their findings to the authorities. If they encounter new phishing scams, for instance, they can send related URLs, IP addresses, and email addresses to blocklists so other users can avoid them.
Informing the Internet service provider (ISP) or RIR that assigned an IP address to the offender is also recommended. In some countries like the U.S., the Federal Trade Commission (FTC) encourages users to submit phishing email samples to the Anti-Phishing Work Group (APWG), text messages to SPAM (7726), and report cases to its complaint portal.
These establishments are authorized to take necessary action against offenders, including taking down proven phishing websites, denying offenders the right to own domains, and even filing cybercriminal charges against them.
Stage 4: Follow-Up Monitoring
The buck doesn’t stop at catching culprits red-handed, though. Securing one’s online properties from phishing is an ongoing battle. When phishing sites are blocked, their owners just register new ones under new identities and/or with new credentials. Creating a new email address and website, after all, only takes a few minutes.
That is why users must now always be on the lookout for known threats or ones that get reported in the news. They should be wary of unknown dangers, too. Armed with a list of cybercriminal identities (names, whether real or fake), domains, organizations (regardless of legitimacy), email addresses, and IP addresses, users can track new developments and stay safe from threats with the help of monitoring solutions such as Registrant Alert API/Registrant Monitor.
In our example, users can monitor the registrant’s (Oleg Ivlev) activities by adding his name to a monitoring tool that will alert them every time he registers a domain. Should he be a confirmed cybercriminal based on the authorities’ conclusion, of course, all succeeding domains that he owns should be avoided and blacklisted.
Conclusion
Staying safe from all kinds of threats is a multi-pronged process. While it may seem tedious to some, domain research and monitoring supported by adequate cyber threat intelligence is a critical procedure if users wish to thwart widespread threats like phishing. Sadly, the ever-increasing sophistication of cyber attackers can no longer be addressed by even the most discerning users without the help of reliable solutions.



































